监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:RCE
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-CVE-2025-6384
标签:#RCE
更新了:RCE
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-CVE-2025-6384
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-Groovy-RCE---CVE-2025-6384
标签:#CVE-2025
更新了:CVE-2025
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-Groovy-RCE---CVE-2025-6384
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:🔍 Discover a security risk in GraalVM Espresso JDK that enables RCE by exploiting the Continuation API with a simple gadget.
URL:https://github.com/Sinthiya-Prapti/hacking-espresso
标签:#RCE
更新了:RCE
描述:🔍 Discover a security risk in GraalVM Espresso JDK that enables RCE by exploiting the Continuation API with a simple gadget.
URL:https://github.com/Sinthiya-Prapti/hacking-espresso
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-20352 SNMP Exposure Check (onesixtyone + parser)
URL:https://github.com/scadastrangelove/CVE-2025-20352
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-20352 SNMP Exposure Check (onesixtyone + parser)
URL:https://github.com/scadastrangelove/CVE-2025-20352
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-49132
URL:https://github.com/WebSafety-2tina/CVE-2025-49132
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-49132
URL:https://github.com/WebSafety-2tina/CVE-2025-49132
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2025-51591-Pandoc-SSRF-POC
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2025-51591-Pandoc-SSRF-POC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2022-35583-Pandoc-SSRF-POC
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2022-35583-Pandoc-SSRF-POC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:绕过
描述:使用 Python 在 Selenium 中绕过 CAPTCHA。本指南涵盖反检测(Stealth)技术、浏览器自动化与代理集成,帮助避免被检测。
URL:https://github.com/bright-cn/bypass-captcha-with-selenium
标签:#绕过
更新了:绕过
描述:使用 Python 在 Selenium 中绕过 CAPTCHA。本指南涵盖反检测(Stealth)技术、浏览器自动化与代理集成,帮助避免被检测。
URL:https://github.com/bright-cn/bypass-captcha-with-selenium
标签:#绕过
GitHub监控消息提醒!!!
更新了:绕过
描述:使用反检测(Stealth)技术、浏览器自动化与 CAPTCHA 解决方案,在 Playwright 中绕过 CAPTCHA,实现无缝的网页抓取与测试。
URL:https://github.com/bright-cn/bypass-captcha-with-playwright
标签:#绕过
更新了:绕过
描述:使用反检测(Stealth)技术、浏览器自动化与 CAPTCHA 解决方案,在 Playwright 中绕过 CAPTCHA,实现无缝的网页抓取与测试。
URL:https://github.com/bright-cn/bypass-captcha-with-playwright
标签:#绕过
GitHub监控消息提醒!!!
更新了:RCE
描述:Full writeup for the Hack The Box machine \"Lame\" – root via Samba RCE using Metasploit
URL:https://github.com/svesec/htb-lame
标签:#RCE
更新了:RCE
描述:Full writeup for the Hack The Box machine \"Lame\" – root via Samba RCE using Metasploit
URL:https://github.com/svesec/htb-lame
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/lucyna77/winrar-malware-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/lucyna77/winrar-malware-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/0x721658/winrar-malware-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/0x721658/winrar-malware-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:⚠️ Demonstrate CVE-2025-55188 with this proof-of-concept exploit for 7-Zip, revealing vulnerabilities in file extraction handling and potential impacts.
URL:https://github.com/Sh3ruman/CVE-2025-55188-7z-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:⚠️ Demonstrate CVE-2025-55188 with this proof-of-concept exploit for 7-Zip, revealing vulnerabilities in file extraction handling and potential impacts.
URL:https://github.com/Sh3ruman/CVE-2025-55188-7z-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-57176 - Siklu EtherHaul Series - Unauthenticated Arbitrary File Upload
URL:https://github.com/semaja22/CVE-2025-57176
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-57176 - Siklu EtherHaul Series - Unauthenticated Arbitrary File Upload
URL:https://github.com/semaja22/CVE-2025-57176
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-57174 Unauthenticated Remote Command Execution
URL:https://github.com/semaja22/CVE-2025-57174
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-57174 Unauthenticated Remote Command Execution
URL:https://github.com/semaja22/CVE-2025-57174
标签:#CVE-2025
GitHub监控消息提醒!!!
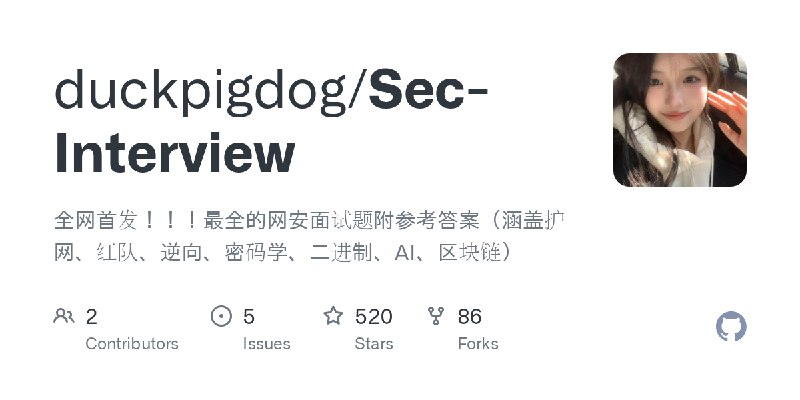
更新了:护网
描述:全网首发!!!上网道网安面试题总结(涵盖护网、渗透、红队、逆向、密码、二进制、区块链、AI、云)
URL:https://github.com/duckpigdog/Sec-Interview
标签:#护网
更新了:护网
描述:全网首发!!!上网道网安面试题总结(涵盖护网、渗透、红队、逆向、密码、二进制、区块链、AI、云)
URL:https://github.com/duckpigdog/Sec-Interview
标签:#护网
GitHub监控消息提醒!!!
更新了:权限提升
描述:Wiki漏洞库管理系统&网络安全知识库-渗透测试常见漏洞知识库文档-该网站收集了Web应用层漏洞、中间件安全缺陷、系统配置不当、移动端(Android)安全问题、权限提升、RCE、网络设备及IOT安全。
URL:https://github.com/qijun1900/MiaowTest
标签:#权限提升
更新了:权限提升
描述:Wiki漏洞库管理系统&网络安全知识库-渗透测试常见漏洞知识库文档-该网站收集了Web应用层漏洞、中间件安全缺陷、系统配置不当、移动端(Android)安全问题、权限提升、RCE、网络设备及IOT安全。
URL:https://github.com/qijun1900/MiaowTest
标签:#权限提升