监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Xss In Tawk.to Live Chat Support (CVE-2025-57483)
URL:https://github.com/Jainil-89/CVE
标签:#CVE-2025
更新了:CVE-2025
描述:Xss In Tawk.to Live Chat Support (CVE-2025-57483)
URL:https://github.com/Jainil-89/CVE
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:burp
描述:burpsuite attempt with a tryhackme lab
URL:https://github.com/shelby628/burpsuite-trial
标签:#burp
更新了:burp
描述:burpsuite attempt with a tryhackme lab
URL:https://github.com/shelby628/burpsuite-trial
标签:#burp
GitHub监控消息提醒!!!
更新了:漏洞检测
描述: 这是一个基于Django框架开发的内部网络资产发现与管理工具,专门用于自动化发现、监控和管理企业内部网络中的各种资产设备。系统集成了多种网络扫描技术,提供实时资产状态监控、漏洞检测、告警管理等功能。
URL:https://github.com/968626/Internal-Network-Asset-Discovery-and-Management-Tool
标签:#漏洞检测
更新了:漏洞检测
描述: 这是一个基于Django框架开发的内部网络资产发现与管理工具,专门用于自动化发现、监控和管理企业内部网络中的各种资产设备。系统集成了多种网络扫描技术,提供实时资产状态监控、漏洞检测、告警管理等功能。
URL:https://github.com/968626/Internal-Network-Asset-Discovery-and-Management-Tool
标签:#漏洞检测
GitHub监控消息提醒!!!
更新了:RCE
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-CVE-2025-6384
标签:#RCE
更新了:RCE
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-CVE-2025-6384
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-Groovy-RCE---CVE-2025-6384
标签:#CVE-2025
更新了:CVE-2025
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-Groovy-RCE---CVE-2025-6384
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:🔍 Discover a security risk in GraalVM Espresso JDK that enables RCE by exploiting the Continuation API with a simple gadget.
URL:https://github.com/Sinthiya-Prapti/hacking-espresso
标签:#RCE
更新了:RCE
描述:🔍 Discover a security risk in GraalVM Espresso JDK that enables RCE by exploiting the Continuation API with a simple gadget.
URL:https://github.com/Sinthiya-Prapti/hacking-espresso
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-20352 SNMP Exposure Check (onesixtyone + parser)
URL:https://github.com/scadastrangelove/CVE-2025-20352
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-20352 SNMP Exposure Check (onesixtyone + parser)
URL:https://github.com/scadastrangelove/CVE-2025-20352
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-49132
URL:https://github.com/WebSafety-2tina/CVE-2025-49132
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-49132
URL:https://github.com/WebSafety-2tina/CVE-2025-49132
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2025-51591-Pandoc-SSRF-POC
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2025-51591-Pandoc-SSRF-POC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2022-35583-Pandoc-SSRF-POC
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-51591 Pandoc SSRF vulnerability Proof of Concept
URL:https://github.com/Malayke/CVE-2022-35583-Pandoc-SSRF-POC
标签:#CVE-2025
GitHub监控消息提醒!!!
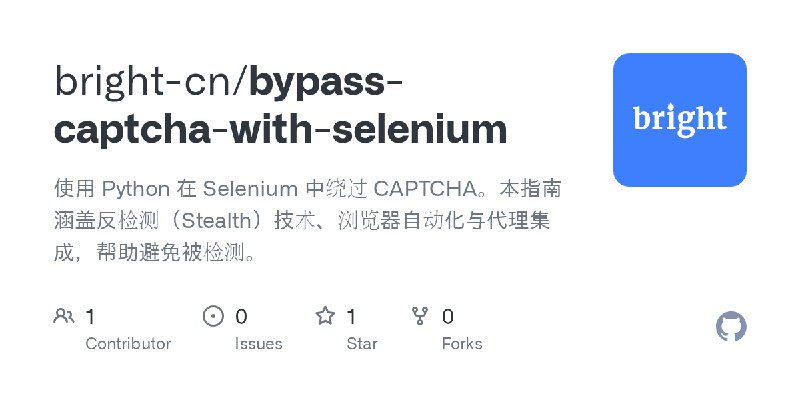
更新了:绕过
描述:使用 Python 在 Selenium 中绕过 CAPTCHA。本指南涵盖反检测(Stealth)技术、浏览器自动化与代理集成,帮助避免被检测。
URL:https://github.com/bright-cn/bypass-captcha-with-selenium
标签:#绕过
更新了:绕过
描述:使用 Python 在 Selenium 中绕过 CAPTCHA。本指南涵盖反检测(Stealth)技术、浏览器自动化与代理集成,帮助避免被检测。
URL:https://github.com/bright-cn/bypass-captcha-with-selenium
标签:#绕过
GitHub监控消息提醒!!!
更新了:绕过
描述:使用反检测(Stealth)技术、浏览器自动化与 CAPTCHA 解决方案,在 Playwright 中绕过 CAPTCHA,实现无缝的网页抓取与测试。
URL:https://github.com/bright-cn/bypass-captcha-with-playwright
标签:#绕过
更新了:绕过
描述:使用反检测(Stealth)技术、浏览器自动化与 CAPTCHA 解决方案,在 Playwright 中绕过 CAPTCHA,实现无缝的网页抓取与测试。
URL:https://github.com/bright-cn/bypass-captcha-with-playwright
标签:#绕过
GitHub监控消息提醒!!!
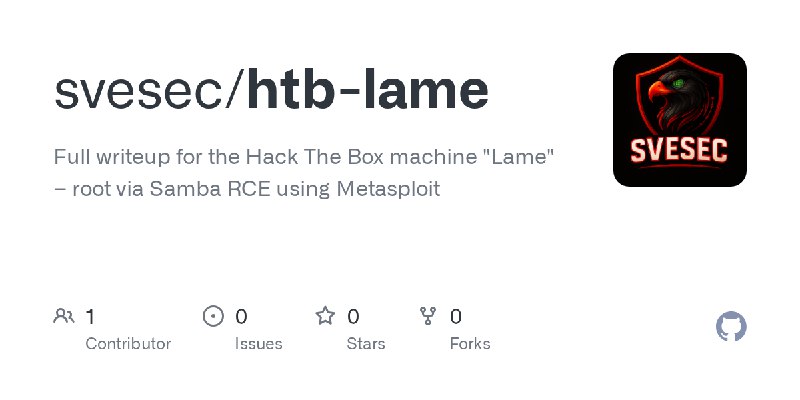
更新了:RCE
描述:Full writeup for the Hack The Box machine \"Lame\" – root via Samba RCE using Metasploit
URL:https://github.com/svesec/htb-lame
标签:#RCE
更新了:RCE
描述:Full writeup for the Hack The Box machine \"Lame\" – root via Samba RCE using Metasploit
URL:https://github.com/svesec/htb-lame
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/lucyna77/winrar-malware-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/lucyna77/winrar-malware-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/0x721658/winrar-malware-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 exploit C++ impl
URL:https://github.com/0x721658/winrar-malware-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:⚠️ Demonstrate CVE-2025-55188 with this proof-of-concept exploit for 7-Zip, revealing vulnerabilities in file extraction handling and potential impacts.
URL:https://github.com/Sh3ruman/CVE-2025-55188-7z-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:⚠️ Demonstrate CVE-2025-55188 with this proof-of-concept exploit for 7-Zip, revealing vulnerabilities in file extraction handling and potential impacts.
URL:https://github.com/Sh3ruman/CVE-2025-55188-7z-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-57176 - Siklu EtherHaul Series - Unauthenticated Arbitrary File Upload
URL:https://github.com/semaja22/CVE-2025-57176
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-57176 - Siklu EtherHaul Series - Unauthenticated Arbitrary File Upload
URL:https://github.com/semaja22/CVE-2025-57176
标签:#CVE-2025