监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:RCE
描述:基于alpine+php7.3的一个RCE命令执行靶场,包含基础命令、shell 特性、常见姿势、常见waf绕过
URL:https://github.com/Apursuit/rce-labs
标签:#RCE
更新了:RCE
描述:基于alpine+php7.3的一个RCE命令执行靶场,包含基础命令、shell 特性、常见姿势、常见waf绕过
URL:https://github.com/Apursuit/rce-labs
标签:#RCE
GitHub监控消息提醒!!!
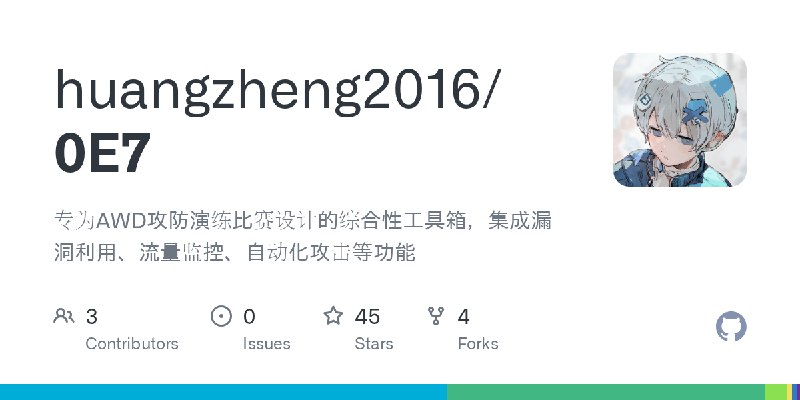
更新了:漏洞利用
描述:专为AWD攻防演练比赛设计的综合性工具箱,集成漏洞利用、流量监控、自动化攻击等功能
URL:https://github.com/huangzheng2016/0E7
标签:#漏洞利用
更新了:漏洞利用
描述:专为AWD攻防演练比赛设计的综合性工具箱,集成漏洞利用、流量监控、自动化攻击等功能
URL:https://github.com/huangzheng2016/0E7
标签:#漏洞利用
GitHub监控消息提醒!!!
更新了:绕过
描述:小型密码管理器,保存密码后,设置每周三、周五、周六指定时间段才可以查看,可防止修改系统时间绕过检测。
URL:https://github.com/boldiy/password-locker
标签:#绕过
更新了:绕过
描述:小型密码管理器,保存密码后,设置每周三、周五、周六指定时间段才可以查看,可防止修改系统时间绕过检测。
URL:https://github.com/boldiy/password-locker
标签:#绕过
GitHub监控消息提醒!!!
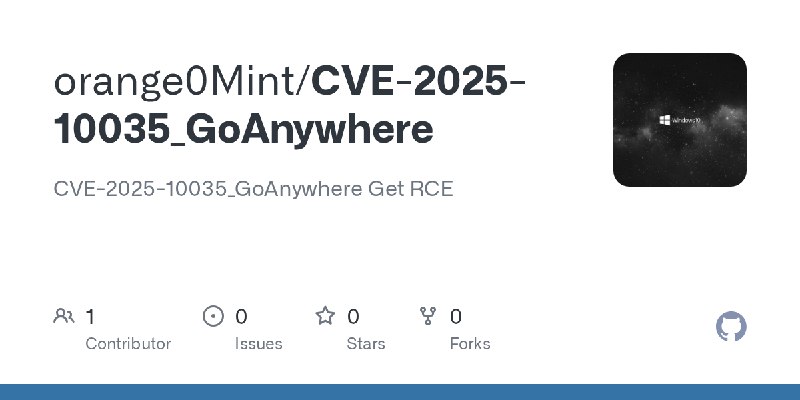
更新了:CVE-2025
描述:CVE-2025-10035_GoAnywhere Get RCE
URL:https://github.com/orange0Mint/CVE-2025-10035_GoAnywhere
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-10035_GoAnywhere Get RCE
URL:https://github.com/orange0Mint/CVE-2025-10035_GoAnywhere
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
URL:https://github.com/umxr286/ExploitScript
标签:#CVE-2025
更新了:CVE-2025
描述:This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
URL:https://github.com/umxr286/ExploitScript
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:🛠️ Reproduce and validate CVE-2025-3515 by setting up a Dockerized WordPress lab for testing unrestricted file uploads in a vulnerable plugin.
URL:https://github.com/robertskimengote/lab-cve-2025-3515
标签:#RCE
更新了:RCE
描述:🛠️ Reproduce and validate CVE-2025-3515 by setting up a Dockerized WordPress lab for testing unrestricted file uploads in a vulnerable plugin.
URL:https://github.com/robertskimengote/lab-cve-2025-3515
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Scans target to see if its vulnerable to CVE-2025-31161
URL:https://github.com/Teexo/CVE-2025-31161
标签:#CVE-2025
更新了:CVE-2025
描述:Scans target to see if its vulnerable to CVE-2025-31161
URL:https://github.com/Teexo/CVE-2025-31161
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🔍 Exploit CVE-2025-5419 to understand its impact and develop effective mitigation strategies for enhanced software security.
URL:https://github.com/somprasong-tukman/CVE-2025-5419
标签:#CVE-2025
更新了:CVE-2025
描述:🔍 Exploit CVE-2025-5419 to understand its impact and develop effective mitigation strategies for enhanced software security.
URL:https://github.com/somprasong-tukman/CVE-2025-5419
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Proof of concept for CVE-2025-39866 (UAF and race condition)
URL:https://github.com/byteReaper77/CVE-2025-39866
标签:#CVE-2025
更新了:CVE-2025
描述:Proof of concept for CVE-2025-39866 (UAF and race condition)
URL:https://github.com/byteReaper77/CVE-2025-39866
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 based path traversal tool
URL:https://github.com/kyomber/CVE-2025-8088
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 based path traversal tool
URL:https://github.com/kyomber/CVE-2025-8088
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Xss In Tawk.to Live Chat Support (CVE-2025-57483)
URL:https://github.com/Jainil-89/CVE
标签:#CVE-2025
更新了:CVE-2025
描述:Xss In Tawk.to Live Chat Support (CVE-2025-57483)
URL:https://github.com/Jainil-89/CVE
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:burp
描述:burpsuite attempt with a tryhackme lab
URL:https://github.com/shelby628/burpsuite-trial
标签:#burp
更新了:burp
描述:burpsuite attempt with a tryhackme lab
URL:https://github.com/shelby628/burpsuite-trial
标签:#burp
GitHub监控消息提醒!!!
更新了:漏洞检测
描述: 这是一个基于Django框架开发的内部网络资产发现与管理工具,专门用于自动化发现、监控和管理企业内部网络中的各种资产设备。系统集成了多种网络扫描技术,提供实时资产状态监控、漏洞检测、告警管理等功能。
URL:https://github.com/968626/Internal-Network-Asset-Discovery-and-Management-Tool
标签:#漏洞检测
更新了:漏洞检测
描述: 这是一个基于Django框架开发的内部网络资产发现与管理工具,专门用于自动化发现、监控和管理企业内部网络中的各种资产设备。系统集成了多种网络扫描技术,提供实时资产状态监控、漏洞检测、告警管理等功能。
URL:https://github.com/968626/Internal-Network-Asset-Discovery-and-Management-Tool
标签:#漏洞检测
GitHub监控消息提醒!!!
更新了:RCE
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-CVE-2025-6384
标签:#RCE
更新了:RCE
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-CVE-2025-6384
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-Groovy-RCE---CVE-2025-6384
标签:#CVE-2025
更新了:CVE-2025
描述:PoC exploit for an authenticated RCE in CrafterCMS via Groovy sandbox bypass (CVE-2025-6384)
URL:https://github.com/maestro-ant/CrafterCMS-Groovy-RCE---CVE-2025-6384
标签:#CVE-2025