监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:RCE
描述:V8 Store-Store Elimination RCE without heap sandbox.
URL:https://github.com/ntLocalSystem/V8-Store-Store-Elimination-Exploit
标签:#RCE
更新了:RCE
描述:V8 Store-Store Elimination RCE without heap sandbox.
URL:https://github.com/ntLocalSystem/V8-Store-Store-Elimination-Exploit
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🚨 Exploit the CVE-2025-49844 Redis Lua interpreter UAF vulnerability to execute arbitrary shellcode and gain persistent backdoor access.
URL:https://github.com/yonatanasd232132/talkingBen
标签:#CVE-2025
更新了:CVE-2025
描述:🚨 Exploit the CVE-2025-49844 Redis Lua interpreter UAF vulnerability to execute arbitrary shellcode and gain persistent backdoor access.
URL:https://github.com/yonatanasd232132/talkingBen
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Helps defenders find their WSUS configurations in the wake of CVE-2025-59287
URL:https://github.com/mubix/Find-WSUS
标签:#CVE-2025
更新了:CVE-2025
描述:Helps defenders find their WSUS configurations in the wake of CVE-2025-59287
URL:https://github.com/mubix/Find-WSUS
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Disclosure for CVE-2025-61156, an insecure access control, kernel-mode vulnerability found in ThreatFire System Monitor abused in the wild for BYOVD and EDR evasion.
URL:https://github.com/D7EAD/CVE-2025-61156
标签:#CVE-2025
更新了:CVE-2025
描述:Disclosure for CVE-2025-61156, an insecure access control, kernel-mode vulnerability found in ThreatFire System Monitor abused in the wild for BYOVD and EDR evasion.
URL:https://github.com/D7EAD/CVE-2025-61156
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🚨 CVE-2025-61884 — High-Risk Oracle EBS Configurator Info Disclosure
URL:https://github.com/AshrafZaryouh/CVE-2025-61884-At-a-Glance
标签:#CVE-2025
更新了:CVE-2025
描述:🚨 CVE-2025-61884 — High-Risk Oracle EBS Configurator Info Disclosure
URL:https://github.com/AshrafZaryouh/CVE-2025-61884-At-a-Glance
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-61882 — Critical Oracle EBS RCE: Analysis & Response
URL:https://github.com/AshrafZaryouh/CVE-2025-61882-Executive-Summary
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-61882 — Critical Oracle EBS RCE: Analysis & Response
URL:https://github.com/AshrafZaryouh/CVE-2025-61882-Executive-Summary
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Module PowerShell de réponse à l'incident CVE-2025-59287 — WSUS Remote Code Execution (RCE)
URL:https://github.com/RadzaRr/WSUSResponder
标签:#CVE-2025
更新了:CVE-2025
描述:Module PowerShell de réponse à l'incident CVE-2025-59287 — WSUS Remote Code Execution (RCE)
URL:https://github.com/RadzaRr/WSUSResponder
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:Cleanest, no RCE, xworm 6.5
URL:https://github.com/ledjonponari/Xworm6.5
标签:#RCE
更新了:RCE
描述:Cleanest, no RCE, xworm 6.5
URL:https://github.com/ledjonponari/Xworm6.5
标签:#RCE
GitHub监控消息提醒!!!
更新了:绕过
描述:绕过谷歌服务证书校验 / Bypass Google Service License Verification
URL:https://github.com/JiGuroLGC/FuckGoogleLicense
标签:#绕过
更新了:绕过
描述:绕过谷歌服务证书校验 / Bypass Google Service License Verification
URL:https://github.com/JiGuroLGC/FuckGoogleLicense
标签:#绕过
GitHub监控消息提醒!!!
更新了:绕过
描述:用来绕过《苍蓝誓约》的版本更新和别的什么验证的服务器程序
URL:https://github.com/xys20071111/BlueOath-fake-server
标签:#绕过
更新了:绕过
描述:用来绕过《苍蓝誓约》的版本更新和别的什么验证的服务器程序
URL:https://github.com/xys20071111/BlueOath-fake-server
标签:#绕过
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Pixnapping Attack: Compromising private keys and seed phrases through vulnerability CVE-2025-48561 represents a new critical threat to the Bitcoin network and Android infrastructure
URL:https://github.com/Lupovis/Honeypot-for-CVE-2025-59287-WSUS
标签:#CVE-2025
更新了:CVE-2025
描述:Pixnapping Attack: Compromising private keys and seed phrases through vulnerability CVE-2025-48561 represents a new critical threat to the Bitcoin network and Android infrastructure
URL:https://github.com/Lupovis/Honeypot-for-CVE-2025-59287-WSUS
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:data stories RCE
URL:https://github.com/danielvflores/rce-java-vulnerability
标签:#RCE
更新了:RCE
描述:data stories RCE
URL:https://github.com/danielvflores/rce-java-vulnerability
标签:#RCE
GitHub监控消息提醒!!!
更新了:漏洞扫描
描述:针对 postmessage xss 的漏洞扫描器
URL:https://github.com/bitboy-sys/postmessage_xss_scanner
标签:#漏洞扫描
更新了:漏洞扫描
描述:针对 postmessage xss 的漏洞扫描器
URL:https://github.com/bitboy-sys/postmessage_xss_scanner
标签:#漏洞扫描
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Pixnapping Attack: Compromising private keys and seed phrases through vulnerability CVE-2025-48561 represents a new critical threat to the Bitcoin network and Android infrastructure
URL:https://github.com/demining/Pixnapping-Attack-on-Android
标签:#CVE-2025
更新了:CVE-2025
描述:Pixnapping Attack: Compromising private keys and seed phrases through vulnerability CVE-2025-48561 represents a new critical threat to the Bitcoin network and Android infrastructure
URL:https://github.com/demining/Pixnapping-Attack-on-Android
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🚨 Exploit the CVE-2025-49844 Redis Lua interpreter UAF vulnerability to execute arbitrary shellcode and gain persistent backdoor access.
URL:https://github.com/Zain3311/CVE-2025-49844
标签:#CVE-2025
更新了:CVE-2025
描述:🚨 Exploit the CVE-2025-49844 Redis Lua interpreter UAF vulnerability to execute arbitrary shellcode and gain persistent backdoor access.
URL:https://github.com/Zain3311/CVE-2025-49844
标签:#CVE-2025
GitHub监控消息提醒!!!
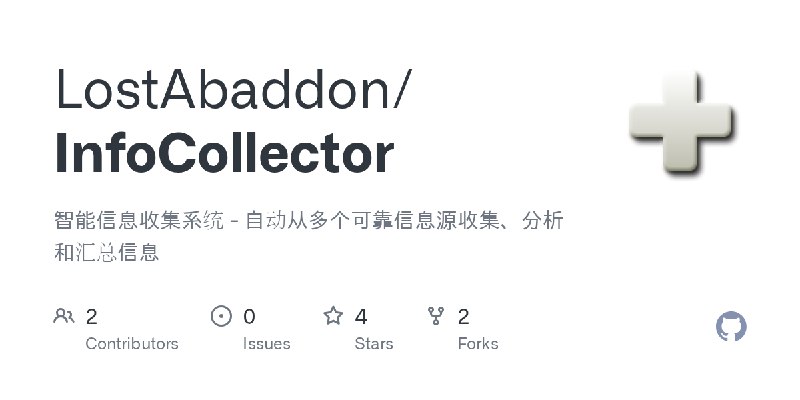
更新了:信息收集
描述:智能信息收集系统 - 自动从多个可靠信息源收集、分析和汇总信息
URL:https://github.com/LostAbaddon/InfoCollector
标签:#信息收集
更新了:信息收集
描述:智能信息收集系统 - 自动从多个可靠信息源收集、分析和汇总信息
URL:https://github.com/LostAbaddon/InfoCollector
标签:#信息收集
GitHub监控消息提醒!!!
更新了:横向移动
描述:Langflow 在对用户提交的“验证代码”做 AST 解析和编译时,在未做鉴权与沙箱限制的情况下调用了 Python 的 compile()/exec()(以及在编译阶段会评估函数默认参数与装饰器),攻击者可把恶意载荷放在参数默认值或装饰器里,借此在服务器上下文中执行任意语句(反弹 shell、下载器、横向移动等)
URL:https://github.com/999999999to1/ProfilePage
标签:#横向移动
更新了:横向移动
描述:Langflow 在对用户提交的“验证代码”做 AST 解析和编译时,在未做鉴权与沙箱限制的情况下调用了 Python 的 compile()/exec()(以及在编译阶段会评估函数默认参数与装饰器),攻击者可把恶意载荷放在参数默认值或装饰器里,借此在服务器上下文中执行任意语句(反弹 shell、下载器、横向移动等)
URL:https://github.com/999999999to1/ProfilePage
标签:#横向移动
GitHub监控消息提醒!!!
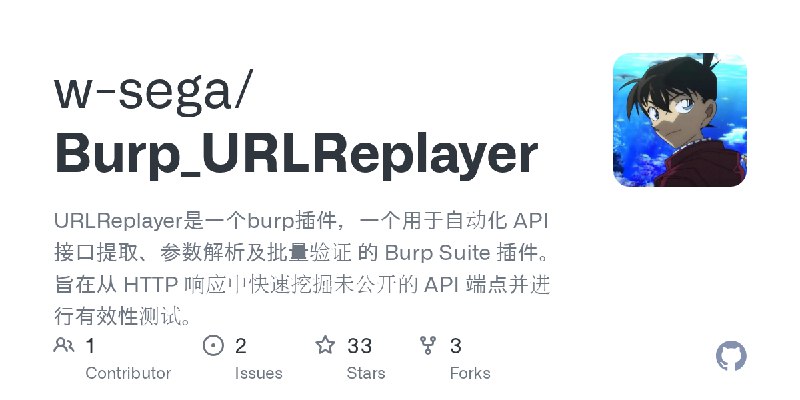
更新了:漏洞验证
描述:URLReplayer是一个burp插件,用于监听匹配所有响应中的接口,拼接来源地址,提供一键发送请求的功能,用于快速验证未授权漏洞
URL:https://github.com/w-sega/Burp_URLReplayer
标签:#漏洞验证
更新了:漏洞验证
描述:URLReplayer是一个burp插件,用于监听匹配所有响应中的接口,拼接来源地址,提供一键发送请求的功能,用于快速验证未授权漏洞
URL:https://github.com/w-sega/Burp_URLReplayer
标签:#漏洞验证
GitHub监控消息提醒!!!
更新了:反序列化
描述:Spring Boot Redis 自动序列化与反序列化配置
URL:https://github.com/xuxiaowei-com-cn/redis-enable-caching
标签:#反序列化
更新了:反序列化
描述:Spring Boot Redis 自动序列化与反序列化配置
URL:https://github.com/xuxiaowei-com-cn/redis-enable-caching
标签:#反序列化