监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🚨 Exploit the CVE-2025-49844 Redis Lua interpreter UAF vulnerability to execute arbitrary shellcode and gain persistent backdoor access.
URL:https://github.com/git0xLai/React2ShellPoC
标签:#CVE-2025
更新了:CVE-2025
描述:🚨 Exploit the CVE-2025-49844 Redis Lua interpreter UAF vulnerability to execute arbitrary shellcode and gain persistent backdoor access.
URL:https://github.com/git0xLai/React2ShellPoC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:红蓝对抗
描述:Rshell是一款开源的golang编写的支持多平台的C2框架,旨在帮助安服人员渗透测试、红蓝对抗。
URL:https://github.com/muddlelife/windfire
标签:#红蓝对抗
更新了:红蓝对抗
描述:Rshell是一款开源的golang编写的支持多平台的C2框架,旨在帮助安服人员渗透测试、红蓝对抗。
URL:https://github.com/muddlelife/windfire
标签:#红蓝对抗
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-52691
URL:https://github.com/Ashwesker/Ashwesker-CVE-2025-52691
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-52691
URL:https://github.com/Ashwesker/Ashwesker-CVE-2025-52691
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:漏洞检测
描述:AiYue_Pro 是一款专为 Burp Suite 设计的高级被动扫描插件,旨在自动化检测 越权漏洞 (IDOR / Broken Access Control)。 它结合了多账号并发重放、智能染色和 AI 大模型深度分析技术,能够精准识别低权限或未授权账号是否能访问高敏感接口,极大降低了人工测试的成本和误报率。
URL:https://github.com/JohnLone00/AiYue
标签:#漏洞检测
更新了:漏洞检测
描述:AiYue_Pro 是一款专为 Burp Suite 设计的高级被动扫描插件,旨在自动化检测 越权漏洞 (IDOR / Broken Access Control)。 它结合了多账号并发重放、智能染色和 AI 大模型深度分析技术,能够精准识别低权限或未授权账号是否能访问高敏感接口,极大降低了人工测试的成本和误报率。
URL:https://github.com/JohnLone00/AiYue
标签:#漏洞检测
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Detection for CVE-2025-52691
URL:https://github.com/rxerium/CVE-2025-52691
标签:#CVE-2025
更新了:CVE-2025
描述:Detection for CVE-2025-52691
URL:https://github.com/rxerium/CVE-2025-52691
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:Red Team
描述:🛡️ AI Security Platform: Defense (200 engines) + Offense (39K+ payloads) | OWASP LLM Top 10 | Red Team toolkit for AI | Protect & Pentest your LLMs
URL:https://github.com/Iborrareddy/Recon-Enhanced
标签:#Red Team
更新了:Red Team
描述:🛡️ AI Security Platform: Defense (200 engines) + Offense (39K+ payloads) | OWASP LLM Top 10 | Red Team toolkit for AI | Protect & Pentest your LLMs
URL:https://github.com/Iborrareddy/Recon-Enhanced
标签:#Red Team
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC of CVE-2025-27515
URL:https://github.com/joaovicdev/POC-CVE-2025-27515
标签:#CVE-2025
更新了:CVE-2025
描述:PoC of CVE-2025-27515
URL:https://github.com/joaovicdev/POC-CVE-2025-27515
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Remake of CVE-2025-14847 MongoDB vulnerability demonstration
URL:https://github.com/vfa-tuannt/CVE-2025-14847
标签:#CVE-2025
更新了:CVE-2025
描述:Remake of CVE-2025-14847 MongoDB vulnerability demonstration
URL:https://github.com/vfa-tuannt/CVE-2025-14847
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:应急响应
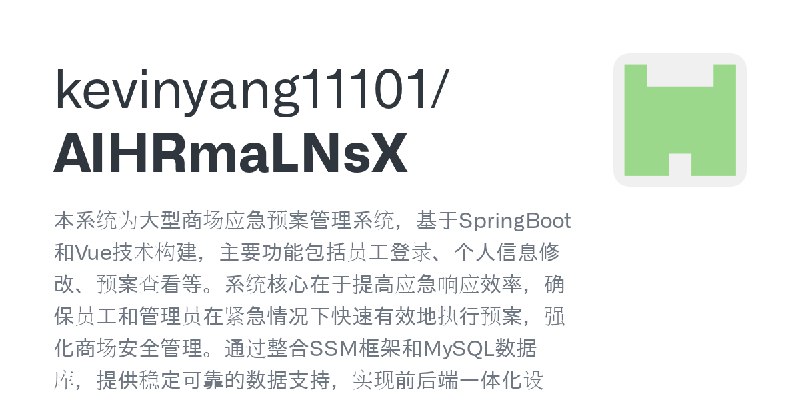
描述:本系统为大型商场应急预案管理系统,基于SpringBoot和Vue技术构建,主要功能包括员工登录、个人信息修改、预案查看等。系统核心在于提高应急响应效率,确保员工和管理员在紧急情况下快速有效地执行预案,强化商场安全管理。通过整合SSM框架和MySQL数据库,提供稳定可靠的数据支持,实现前后端一体化设计,便于远程部署与调试,为商场运营保驾护航。
URL:https://github.com/kevinyang11101/AIHRmaLNsX
标签:#应急响应
更新了:应急响应
描述:本系统为大型商场应急预案管理系统,基于SpringBoot和Vue技术构建,主要功能包括员工登录、个人信息修改、预案查看等。系统核心在于提高应急响应效率,确保员工和管理员在紧急情况下快速有效地执行预案,强化商场安全管理。通过整合SSM框架和MySQL数据库,提供稳定可靠的数据支持,实现前后端一体化设计,便于远程部署与调试,为商场运营保驾护航。
URL:https://github.com/kevinyang11101/AIHRmaLNsX
标签:#应急响应
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Context-Aware Memory Leak Scanner & Exploit for CVE-2025-14847.
URL:https://github.com/tunahantekeoglu/MongoDeepDive
标签:#CVE-2025
更新了:CVE-2025
描述:Context-Aware Memory Leak Scanner & Exploit for CVE-2025-14847.
URL:https://github.com/tunahantekeoglu/MongoDeepDive
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
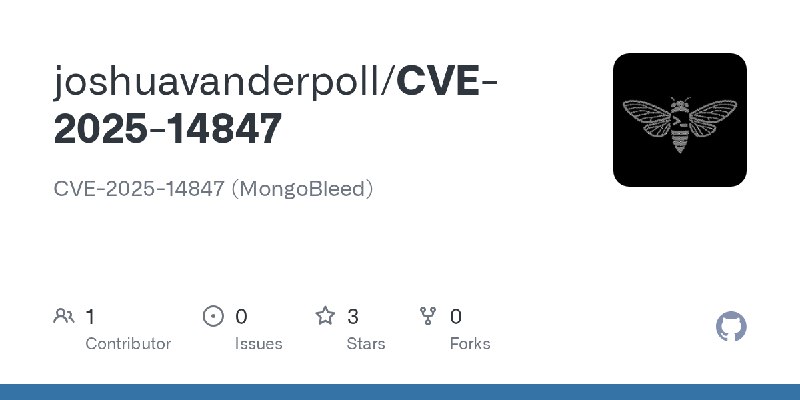
描述:CVE-2025-14847 (MongoBleed)
URL:https://github.com/joshuavanderpoll/CVE-2025-14847
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-14847 (MongoBleed)
URL:https://github.com/joshuavanderpoll/CVE-2025-14847
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🛠️ Exploit CVE-2025-55182 effortlessly with this GUI tool for vulnerability detection, command execution, and Shell reverse connections.
URL:https://github.com/vick333-peniel/ReactExploitGUI
标签:#CVE-2025
更新了:CVE-2025
描述:🛠️ Exploit CVE-2025-55182 effortlessly with this GUI tool for vulnerability detection, command execution, and Shell reverse connections.
URL:https://github.com/vick333-peniel/ReactExploitGUI
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
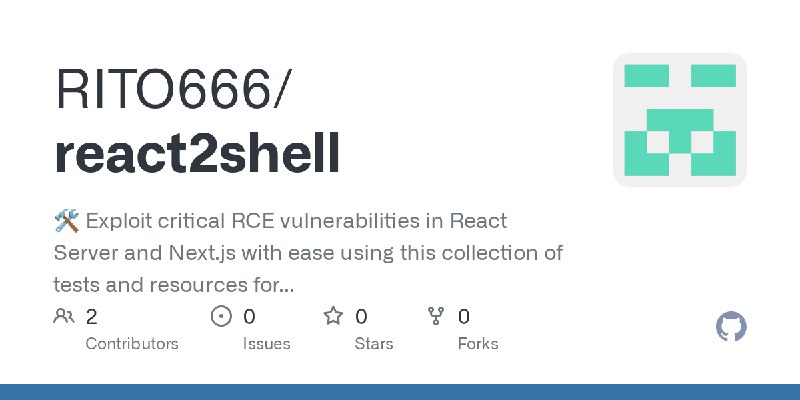
描述:🛠️ Exploit critical RCE vulnerabilities in React Server and Next.js with ease using this collection of tests and resources for security professionals.
URL:https://github.com/RITO666/react2shell
标签:#RCE
更新了:RCE
描述:🛠️ Exploit critical RCE vulnerabilities in React Server and Next.js with ease using this collection of tests and resources for security professionals.
URL:https://github.com/RITO666/react2shell
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:A proof-of-concept exploit for CVE-2025-14847, a critical memory leak vulnerability in MongoDB's OP_COMPRESSED message handler.
URL:https://github.com/ob1sec/mongobleeder
标签:#CVE-2025
更新了:CVE-2025
描述:A proof-of-concept exploit for CVE-2025-14847, a critical memory leak vulnerability in MongoDB's OP_COMPRESSED message handler.
URL:https://github.com/ob1sec/mongobleeder
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🛠️ Exploit CVE-2025-55182 with this GUI tool for vulnerability detection, command execution, and shell access on Windows and macOS systems.
URL:https://github.com/vick333-peniel/vick333-peniel.github.io
标签:#CVE-2025
更新了:CVE-2025
描述:🛠️ Exploit CVE-2025-55182 with this GUI tool for vulnerability detection, command execution, and shell access on Windows and macOS systems.
URL:https://github.com/vick333-peniel/vick333-peniel.github.io
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:🛠️ Explore a toolkit to study Remote Code Execution (RCE) vulnerabilities in Next.js applications, focusing on insecure patterns and misconfigurations.
URL:https://github.com/hrefcoder/Nextjs-RCE-exploit-kit
标签:#RCE
更新了:RCE
描述:🛠️ Explore a toolkit to study Remote Code Execution (RCE) vulnerabilities in Next.js applications, focusing on insecure patterns and misconfigurations.
URL:https://github.com/hrefcoder/Nextjs-RCE-exploit-kit
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-14611 CentreStack and Triofox full Poc/Exploit
URL:https://github.com/pl4tyz/CVE-2025-14611-CentreStack-and-Triofox-full-Poc-Exploit
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-14611 CentreStack and Triofox full Poc/Exploit
URL:https://github.com/pl4tyz/CVE-2025-14611-CentreStack-and-Triofox-full-Poc-Exploit
标签:#CVE-2025