监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC exploit for CVE-2025-48543 in C++
URL:https://github.com/gamesarchive/CVE-2025-48543
标签:#CVE-2025
更新了:CVE-2025
描述:PoC exploit for CVE-2025-48543 in C++
URL:https://github.com/gamesarchive/CVE-2025-48543
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC exploit for CVE-2025-48543 in C++
URL:https://github.com/gamesarchive/CVE-2025-48543
标签:#CVE-2025
更新了:CVE-2025
描述:PoC exploit for CVE-2025-48543 in C++
URL:https://github.com/gamesarchive/CVE-2025-48543
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Proof of concept source code and misc files for my CVE-2025-21692 exploit, kernel version 6.6.75
URL:https://github.com/volticks/CVE-2025-21692-poc
标签:#CVE-2025
更新了:CVE-2025
描述:Proof of concept source code and misc files for my CVE-2025-21692 exploit, kernel version 6.6.75
URL:https://github.com/volticks/CVE-2025-21692-poc
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Proof of concept source code and misc files for my CVE-2025-21692 exploit, kernel version 6.6.75
URL:https://github.com/volticks/CVE-2025-21692-poc
标签:#CVE-2025
更新了:CVE-2025
描述:Proof of concept source code and misc files for my CVE-2025-21692 exploit, kernel version 6.6.75
URL:https://github.com/volticks/CVE-2025-21692-poc
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Safe, read-only SQL Injection checker for FreePBX (CVE-2025-57819), using error/boolean/time-based techniques with per-parameter verdicts and JSON reporting.
URL:https://github.com/xV4nd3Rx/CVE-2025-57819_FreePBX-PoC
标签:#CVE-2025
更新了:CVE-2025
描述:Safe, read-only SQL Injection checker for FreePBX (CVE-2025-57819), using error/boolean/time-based techniques with per-parameter verdicts and JSON reporting.
URL:https://github.com/xV4nd3Rx/CVE-2025-57819_FreePBX-PoC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Safe, read-only SQL Injection checker for FreePBX (CVE-2025-57819), using error/boolean/time-based techniques with per-parameter verdicts and JSON reporting.
URL:https://github.com/xV4nd3Rx/CVE-2025-57819_FreePBX-PoC
标签:#CVE-2025
更新了:CVE-2025
描述:Safe, read-only SQL Injection checker for FreePBX (CVE-2025-57819), using error/boolean/time-based techniques with per-parameter verdicts and JSON reporting.
URL:https://github.com/xV4nd3Rx/CVE-2025-57819_FreePBX-PoC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:webshell
描述:Render Math Equations inside react native using katex inside webshell for dynamic height
URL:https://github.com/ibeginnernoob/react-native-katex
标签:#webshell
更新了:webshell
描述:Render Math Equations inside react native using katex inside webshell for dynamic height
URL:https://github.com/ibeginnernoob/react-native-katex
标签:#webshell
GitHub监控消息提醒!!!
更新了:RCE
描述:This is a simple and benign Go script that red teamers can drop and attempt execution to test RCE on Windows/Linux machines
URL:https://github.com/maverick-doan/rce-checker
标签:#RCE
更新了:RCE
描述:This is a simple and benign Go script that red teamers can drop and attempt execution to test RCE on Windows/Linux machines
URL:https://github.com/maverick-doan/rce-checker
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:This is a simple and benign Go script that red teamers can drop and attempt execution to test RCE on Windows/Linux machines
URL:https://github.com/maverick-doan/rce-checker
标签:#RCE
更新了:RCE
描述:This is a simple and benign Go script that red teamers can drop and attempt execution to test RCE on Windows/Linux machines
URL:https://github.com/maverick-doan/rce-checker
标签:#RCE
GitHub监控消息提醒!!!
更新了:护网
描述:Node.js+Playwright服务器,通过模拟 OpenAI API 的方式来访问 Google AI Studio 网页版,服务器无缝交互转发gemini模型对话。这使得兼容 OpenAI API 的客户端(如 Open WebUI, NextChat 等)可以使用 AI Studio 的无限额度及能力。经测试因无法绕过自动化检测故暂不支持无头模式启动实例-自用项目随缘维护
URL:https://github.com/q211521/Scrapy-Hotel
标签:#护网
更新了:护网
描述:Node.js+Playwright服务器,通过模拟 OpenAI API 的方式来访问 Google AI Studio 网页版,服务器无缝交互转发gemini模型对话。这使得兼容 OpenAI API 的客户端(如 Open WebUI, NextChat 等)可以使用 AI Studio 的无限额度及能力。经测试因无法绕过自动化检测故暂不支持无头模式启动实例-自用项目随缘维护
URL:https://github.com/q211521/Scrapy-Hotel
标签:#护网
GitHub监控消息提醒!!!
更新了:护网
描述:Node.js+Playwright服务器,通过模拟 OpenAI API 的方式来访问 Google AI Studio 网页版,服务器无缝交互转发gemini模型对话。这使得兼容 OpenAI API 的客户端(如 Open WebUI, NextChat 等)可以使用 AI Studio 的无限额度及能力。经测试因无法绕过自动化检测故暂不支持无头模式启动实例-自用项目随缘维护
URL:https://github.com/q211521/Scrapy-Hotel
标签:#护网
更新了:护网
描述:Node.js+Playwright服务器,通过模拟 OpenAI API 的方式来访问 Google AI Studio 网页版,服务器无缝交互转发gemini模型对话。这使得兼容 OpenAI API 的客户端(如 Open WebUI, NextChat 等)可以使用 AI Studio 的无限额度及能力。经测试因无法绕过自动化检测故暂不支持无头模式启动实例-自用项目随缘维护
URL:https://github.com/q211521/Scrapy-Hotel
标签:#护网
GitHub监控消息提醒!!!
更新了:burp
描述:A burp suite extension to add shortcut for encoding & decoding Unicode.
URL:https://github.com/szxcp/Unicode-Shortcut
标签:#burp
更新了:burp
描述:A burp suite extension to add shortcut for encoding & decoding Unicode.
URL:https://github.com/szxcp/Unicode-Shortcut
标签:#burp
GitHub监控消息提醒!!!
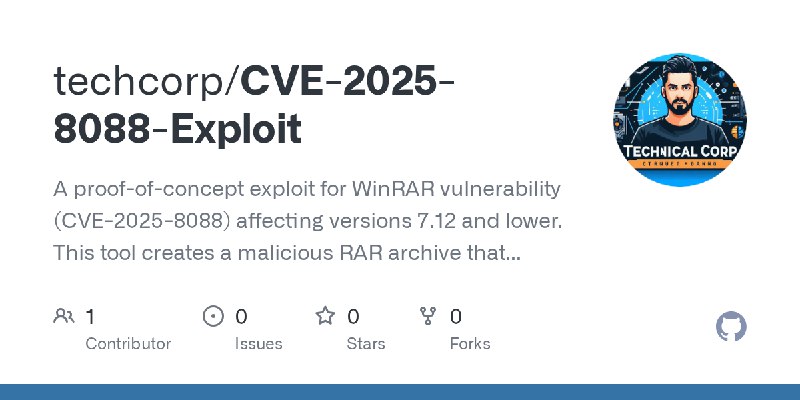
更新了:CVE-2025
描述:This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
URL:https://github.com/techcorp/CVE-2025-8088-Exploit
标签:#CVE-2025
更新了:CVE-2025
描述:This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
URL:https://github.com/techcorp/CVE-2025-8088-Exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
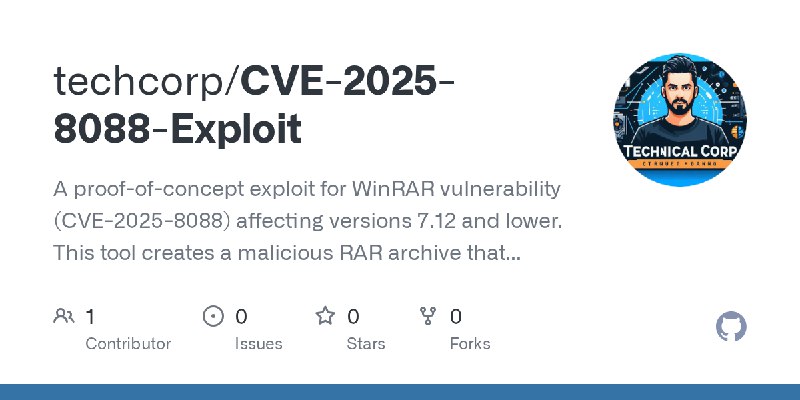
更新了:CVE-2025
描述:This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
URL:https://github.com/techcorp/CVE-2025-8088-Exploit
标签:#CVE-2025
更新了:CVE-2025
描述:This repository contains POC scenarios as part of CVE-2025-0411 MotW bypass.
URL:https://github.com/techcorp/CVE-2025-8088-Exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 path traversal tool
URL:https://github.com/tartalu/CVE-2025-8088
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 path traversal tool
URL:https://github.com/tartalu/CVE-2025-8088
标签:#CVE-2025
GitHub监控消息提醒!!!
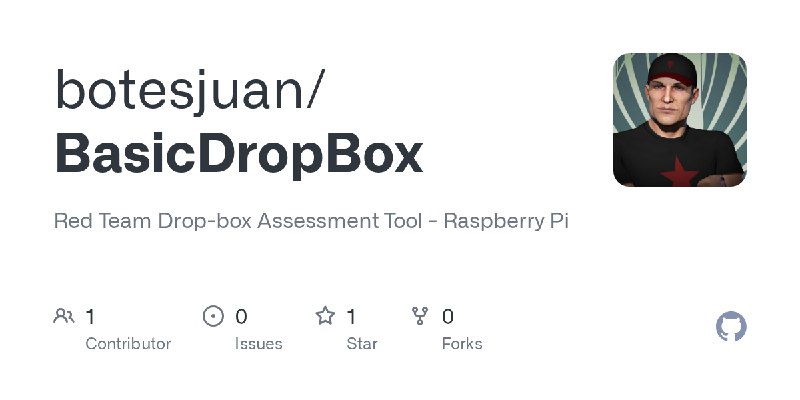
更新了:Red Team
描述:Red Team Drop-box Assessment Tool - Raspberry Pi
URL:https://github.com/botesjuan/BasicDropBox
标签:#Red Team
更新了:Red Team
描述:Red Team Drop-box Assessment Tool - Raspberry Pi
URL:https://github.com/botesjuan/BasicDropBox
标签:#Red Team
GitHub监控消息提醒!!!
更新了:Red Team
描述:Awesome Red Teaming
URL:https://github.com/cybersecurity-dev/awesome-red-teaming
标签:#Red Team
更新了:Red Team
描述:Awesome Red Teaming
URL:https://github.com/cybersecurity-dev/awesome-red-teaming
标签:#Red Team
GitHub监控消息提醒!!!
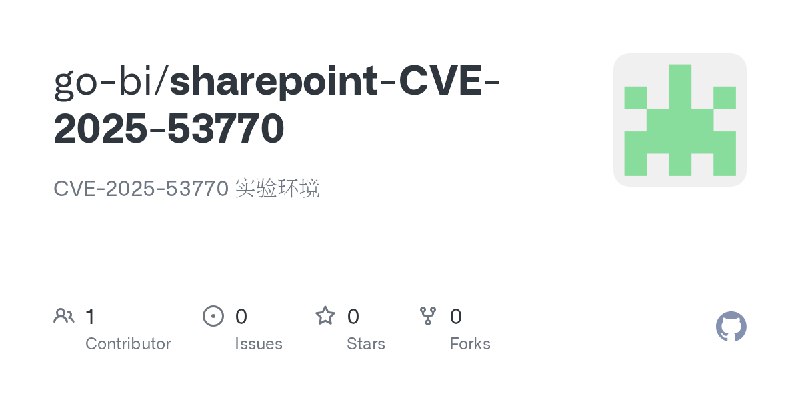
更新了:CVE-2025
描述:CVE-2025-53770 实验环境
URL:https://github.com/go-bi/sharepoint-CVE-2025-53770
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-53770 实验环境
URL:https://github.com/go-bi/sharepoint-CVE-2025-53770
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-53770 实验环境
URL:https://github.com/go-bi/sharepoint-CVE-2025-53770
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-53770 实验环境
URL:https://github.com/go-bi/sharepoint-CVE-2025-53770
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:渗透测试
描述:渗透测试与实验报告(仅限受控实验环境) — 分析、检测线索与防护建议,部分已剔除可复用 exploit 代码。
URL:https://github.com/Brandove-x/Pentest-Project
标签:#渗透测试
更新了:渗透测试
描述:渗透测试与实验报告(仅限受控实验环境) — 分析、检测线索与防护建议,部分已剔除可复用 exploit 代码。
URL:https://github.com/Brandove-x/Pentest-Project
标签:#渗透测试