监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-54424: 1Panel TLS client cert bypass enables RCE via forged CN 'panel_client' using a bundled scanning and exploitation tool. Affected: <= v2.0.5. 🔐
URL:https://github.com/JGoyd/iOS-Attack-Chain-CVE-2025-31200-CVE-2025-31201
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-54424: 1Panel TLS client cert bypass enables RCE via forged CN 'panel_client' using a bundled scanning and exploitation tool. Affected: <= v2.0.5. 🔐
URL:https://github.com/JGoyd/iOS-Attack-Chain-CVE-2025-31200-CVE-2025-31201
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-24893 exploit
URL:https://github.com/ibrahmsql/CVE-2025-24893
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-24893 exploit
URL:https://github.com/ibrahmsql/CVE-2025-24893
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-57617 exploitation
URL:https://github.com/Gooseinpants/Dashy-auth-bypass
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-57617 exploitation
URL:https://github.com/Gooseinpants/Dashy-auth-bypass
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-57617 exploitation
URL:https://github.com/Gooseinpants/Dash-auth-bypass
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-57617 exploitation
URL:https://github.com/Gooseinpants/Dash-auth-bypass
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 based path traversal tool
URL:https://github.com/MoAlali/CVE-2025-56379
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 based path traversal tool
URL:https://github.com/MoAlali/CVE-2025-56379
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:绕过
描述:利用python实现 Microsoft365 E5 Renew X 自动特赦,可绕过自动特赦时间要大于30的限制
URL:https://github.com/OnlineMo/Renew_X_Auto_Pardon
标签:#绕过
更新了:绕过
描述:利用python实现 Microsoft365 E5 Renew X 自动特赦,可绕过自动特赦时间要大于30的限制
URL:https://github.com/OnlineMo/Renew_X_Auto_Pardon
标签:#绕过
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-8088 based path traversal tool
URL:https://github.com/haspread/CVE-2025-8088
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-8088 based path traversal tool
URL:https://github.com/haspread/CVE-2025-8088
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Detection for CVE-2025-41244
URL:https://github.com/rxerium/CVE-2025-41244
标签:#CVE-2025
更新了:CVE-2025
描述:Detection for CVE-2025-41244
URL:https://github.com/rxerium/CVE-2025-41244
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:Backend code for the Brinda RCE Server Manager
URL:https://github.com/intelinsideher/brinda-rce-backend
标签:#RCE
更新了:RCE
描述:Backend code for the Brinda RCE Server Manager
URL:https://github.com/intelinsideher/brinda-rce-backend
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Backend server manager for RCE.js deployment
URL:https://github.com/intelinsideher/rce-server-manager-backend
标签:#RCE
更新了:RCE
描述:Backend server manager for RCE.js deployment
URL:https://github.com/intelinsideher/rce-server-manager-backend
标签:#RCE
GitHub监控消息提醒!!!
更新了:渗透测试
描述:CM Security Tools 是一款模块化、多线程的网络安全扫描工具包,集成主机发现、端口扫描、弱口令检测和子域名枚举等功能,适用于渗透测试与安全研究。
URL:https://github.com/ChildBad/ChicomaloTools
标签:#渗透测试
更新了:渗透测试
描述:CM Security Tools 是一款模块化、多线程的网络安全扫描工具包,集成主机发现、端口扫描、弱口令检测和子域名枚举等功能,适用于渗透测试与安全研究。
URL:https://github.com/ChildBad/ChicomaloTools
标签:#渗透测试
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CPAS audit management information system has SQL injection vulnerability(CVE-2025-57529)
URL:https://github.com/songqb-xx/CVE-2025-57529
标签:#CVE-2025
更新了:CVE-2025
描述:CPAS audit management information system has SQL injection vulnerability(CVE-2025-57529)
URL:https://github.com/songqb-xx/CVE-2025-57529
标签:#CVE-2025
GitHub监控消息提醒!!!
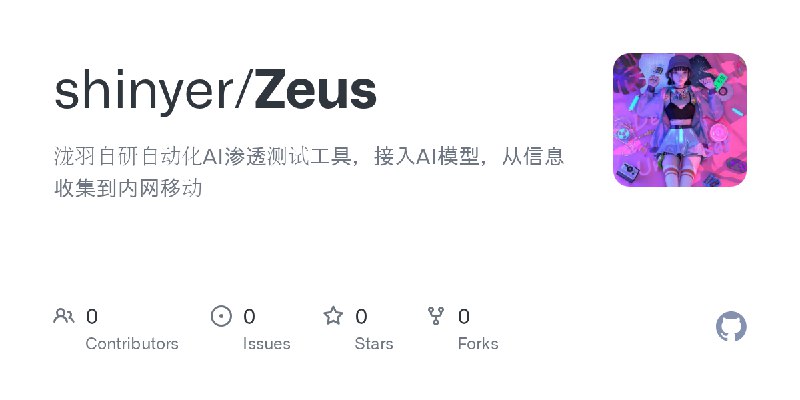
更新了:信息收集
描述:泷羽自研自动化AI渗透测试工具,接入AI模型,从信息收集到内网移动
URL:https://github.com/shinyer/Zeus
标签:#信息收集
更新了:信息收集
描述:泷羽自研自动化AI渗透测试工具,接入AI模型,从信息收集到内网移动
URL:https://github.com/shinyer/Zeus
标签:#信息收集
GitHub监控消息提醒!!!
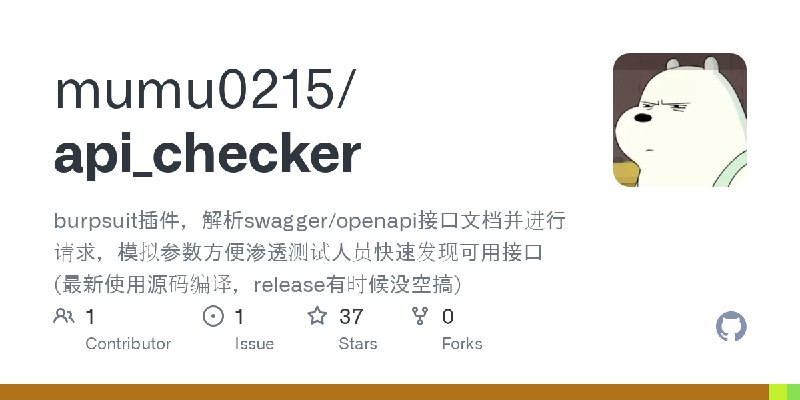
更新了:渗透测试
描述:burpsuit插件,解析swagger/openapi接口文档并进行请求,模拟参数方便渗透测试人员快速发现可用接口
URL:https://github.com/mumu0215/api_checker
标签:#渗透测试
更新了:渗透测试
描述:burpsuit插件,解析swagger/openapi接口文档并进行请求,模拟参数方便渗透测试人员快速发现可用接口
URL:https://github.com/mumu0215/api_checker
标签:#渗透测试
GitHub监控消息提醒!!!
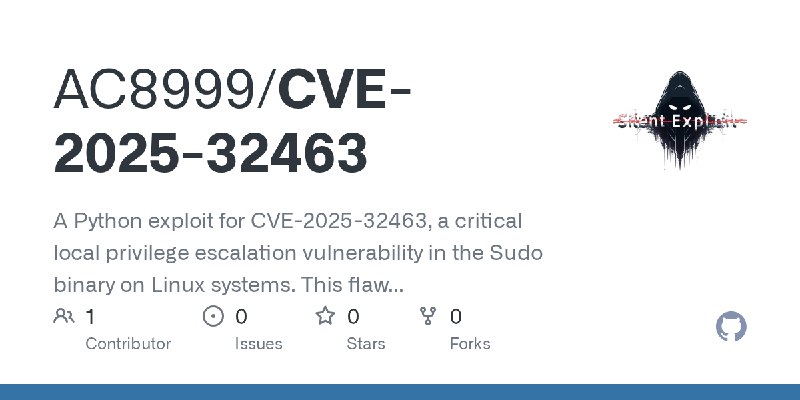
更新了:CVE-2025
描述:A method for CVE-2025-31710 and to connect to cmd_skt to obtain a root shell on unisoc unpatched models
URL:https://github.com/AC8999/CVE-2025-32463
标签:#CVE-2025
更新了:CVE-2025
描述:A method for CVE-2025-31710 and to connect to cmd_skt to obtain a root shell on unisoc unpatched models
URL:https://github.com/AC8999/CVE-2025-32463
标签:#CVE-2025
GitHub监控消息提醒!!!
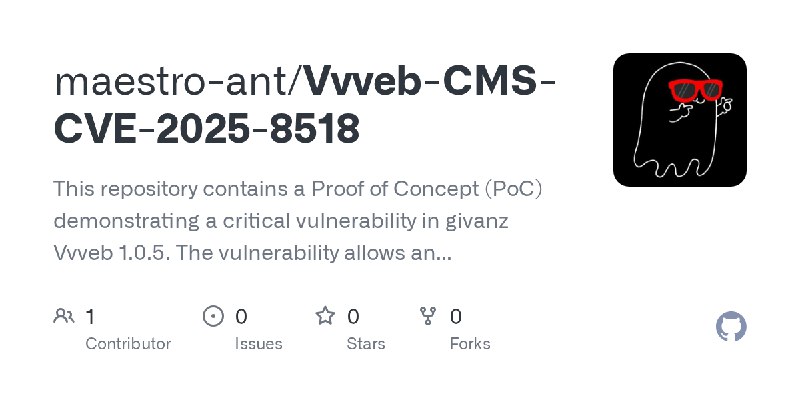
更新了:CVE-2025
描述:🛠️ Reproduce and validate CVE-2025-3515 by setting up a Dockerized WordPress lab for testing unrestricted file uploads in a vulnerable plugin.
URL:https://github.com/maestro-ant/Vvveb-CMS-CVE-2025-8518
标签:#CVE-2025
更新了:CVE-2025
描述:🛠️ Reproduce and validate CVE-2025-3515 by setting up a Dockerized WordPress lab for testing unrestricted file uploads in a vulnerable plugin.
URL:https://github.com/maestro-ant/Vvveb-CMS-CVE-2025-8518
标签:#CVE-2025