监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:渗透测试
描述:AiScan-N 来了!这是一款基于人工智能的Ai全自动化渗透测试工具,专为企业和个人用户打造,尤其适合初学者(小白)快速上手使用,让你轻松迈入智能安全攻防时代!
URL:https://github.com/SecNN/AiScan-N
标签:#渗透测试
更新了:渗透测试
描述:AiScan-N 来了!这是一款基于人工智能的Ai全自动化渗透测试工具,专为企业和个人用户打造,尤其适合初学者(小白)快速上手使用,让你轻松迈入智能安全攻防时代!
URL:https://github.com/SecNN/AiScan-N
标签:#渗透测试
GitHub监控消息提醒!!!
更新了:RCE
描述:A deliberately vulnerable web application demonstrating various SQL injection techniques and PostgreSQL RCE escalation.
URL:https://github.com/tramanh2604/SQL-Injection-Lab
标签:#RCE
更新了:RCE
描述:A deliberately vulnerable web application demonstrating various SQL injection techniques and PostgreSQL RCE escalation.
URL:https://github.com/tramanh2604/SQL-Injection-Lab
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Proof-of-concept for CVE-2025-49844
URL:https://github.com/saneki/cve-2025-49844
标签:#CVE-2025
更新了:CVE-2025
描述:Proof-of-concept for CVE-2025-49844
URL:https://github.com/saneki/cve-2025-49844
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:SQL injection exploit for CVE-2025-26794 in Exim 4.98. Automated data extraction via time-based blind SQLi. For authorized penetration testing only.
URL:https://github.com/XploitGh0st/CVE-2025-26794-exploit
标签:#CVE-2025
更新了:CVE-2025
描述:SQL injection exploit for CVE-2025-26794 in Exim 4.98. Automated data extraction via time-based blind SQLi. For authorized penetration testing only.
URL:https://github.com/XploitGh0st/CVE-2025-26794-exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:IIS-Reverse-Shell uses C++, PHP, HTML, Python, and Ansible to deploy a vulnerable IIS server capable of spawning a reverse shell and Remote Code Execution (RCE) on target machines.
URL:https://github.com/Lcdemi/IIS-Reverse-Shell
标签:#RCE
更新了:RCE
描述:IIS-Reverse-Shell uses C++, PHP, HTML, Python, and Ansible to deploy a vulnerable IIS server capable of spawning a reverse shell and Remote Code Execution (RCE) on target machines.
URL:https://github.com/Lcdemi/IIS-Reverse-Shell
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Proof of Concept for CVE-2025-24367
URL:https://github.com/TheCyberGeek/CVE-2025-24367-Cacti-PoC
标签:#CVE-2025
更新了:CVE-2025
描述:Proof of Concept for CVE-2025-24367
URL:https://github.com/TheCyberGeek/CVE-2025-24367-Cacti-PoC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:PoC for CVE-2025-26625
URL:https://github.com/Mitchellzhou1/CVE_2025_26625
标签:#CVE-2025
更新了:CVE-2025
描述:PoC for CVE-2025-26625
URL:https://github.com/Mitchellzhou1/CVE_2025_26625
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-10035
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-10035
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-10035
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-10035
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:Red Team
描述:Red Teaming Extension for Chrome
URL:https://github.com/delher/RTapp
标签:#Red Team
更新了:Red Team
描述:Red Teaming Extension for Chrome
URL:https://github.com/delher/RTapp
标签:#Red Team
GitHub监控消息提醒!!!
更新了:RCE
描述:A simple script to protect Windows from attacks like SMB RCE
URL:https://github.com/Mr-DS-ML-85/Harden-Windows
标签:#RCE
更新了:RCE
描述:A simple script to protect Windows from attacks like SMB RCE
URL:https://github.com/Mr-DS-ML-85/Harden-Windows
标签:#RCE
GitHub监控消息提醒!!!
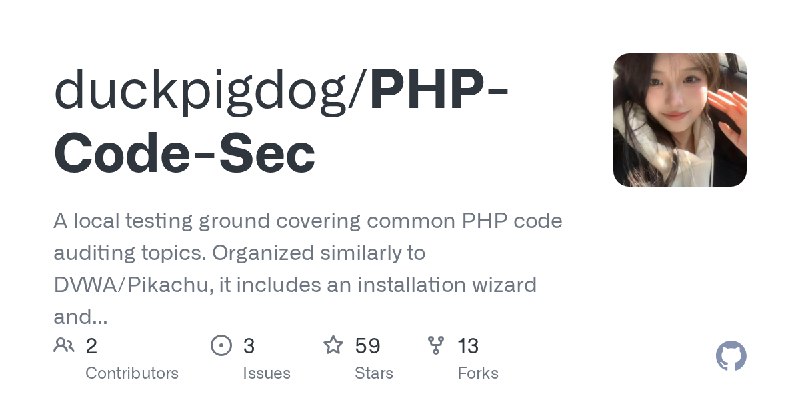
更新了:代码审计
描述:一个覆盖常见 PHP 代码审计知识点的本地靶场。参考 DVWA / Pikachu 的组织方式,含安装向导与通关教程。
URL:https://github.com/duckpigdog/PHP-Code-Sec
标签:#代码审计
更新了:代码审计
描述:一个覆盖常见 PHP 代码审计知识点的本地靶场。参考 DVWA / Pikachu 的组织方式,含安装向导与通关教程。
URL:https://github.com/duckpigdog/PHP-Code-Sec
标签:#代码审计
GitHub监控消息提醒!!!
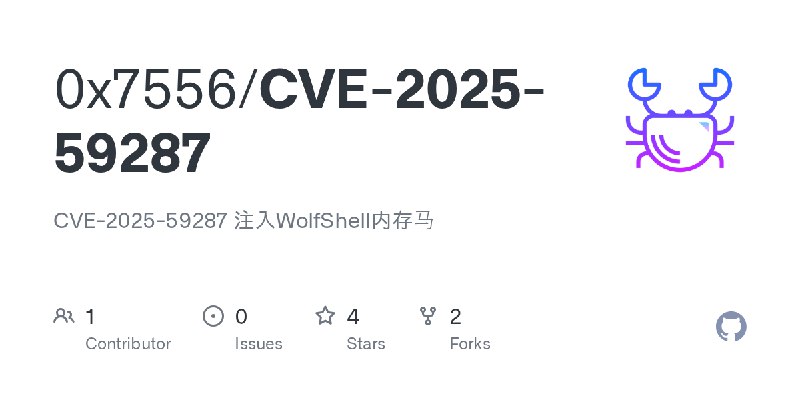
更新了:CVE-2025
描述:CVE-2025-59287 注入WolfShell内存马
URL:https://github.com/0x7556/CVE-2025-59287
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-59287 注入WolfShell内存马
URL:https://github.com/0x7556/CVE-2025-59287
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-55752
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-55752
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-55752
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-55752
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-61481
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-61481
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-61481
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-61481
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-61481
URL:https://github.com/B1ack4sh/CVE-2025-61481
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-61481
URL:https://github.com/B1ack4sh/CVE-2025-61481
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:Red Team
描述:AI Cybersecurity Analyst – Blue & Red Team Assistant for Gemini/ChatGPT
URL:https://github.com/Latowmwo/ShellCode-Encrypt-Tool-Xor-Aes-Fud-Stable
标签:#Red Team
更新了:Red Team
描述:AI Cybersecurity Analyst – Blue & Red Team Assistant for Gemini/ChatGPT
URL:https://github.com/Latowmwo/ShellCode-Encrypt-Tool-Xor-Aes-Fud-Stable
标签:#Red Team
GitHub监控消息提醒!!!
更新了:Cobalt Strike
描述:🔧 Experiment with replacing Cobalt Strike's evasion techniques using Crystal Palace PIC(O)s for enhanced evasion in advanced scenarios.
URL:https://github.com/EndrewDev/Crystal-Kit
标签:#Cobalt Strike
更新了:Cobalt Strike
描述:🔧 Experiment with replacing Cobalt Strike's evasion techniques using Crystal Palace PIC(O)s for enhanced evasion in advanced scenarios.
URL:https://github.com/EndrewDev/Crystal-Kit
标签:#Cobalt Strike