监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
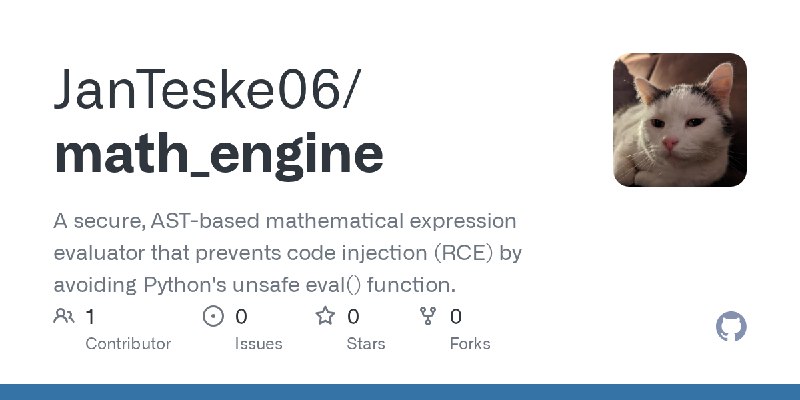
更新了:RCE
描述:A secure, AST-based mathematical expression evaluator that prevents code injection (RCE) by avoiding Python's unsafe eval() function.
URL:https://github.com/JanTeske06/math_engine
标签:#RCE
更新了:RCE
描述:A secure, AST-based mathematical expression evaluator that prevents code injection (RCE) by avoiding Python's unsafe eval() function.
URL:https://github.com/JanTeske06/math_engine
标签:#RCE
GitHub监控消息提醒!!!
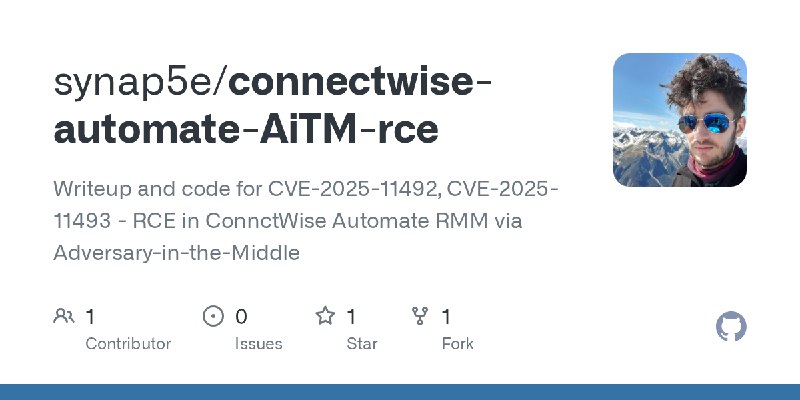
更新了:CVE-2025
描述:Writeup and code for CVE-2025-11492, CVE-2025-11493 - RCE in ConnctWise Automate RMM via Adversary-in-the-Middle
URL:https://github.com/synap5e/connectwise-automate-AiTM-rce
标签:#CVE-2025
更新了:CVE-2025
描述:Writeup and code for CVE-2025-11492, CVE-2025-11493 - RCE in ConnctWise Automate RMM via Adversary-in-the-Middle
URL:https://github.com/synap5e/connectwise-automate-AiTM-rce
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:渗透测试
描述:渗透测试中针对Php Disable_functions的Fpm利用
URL:https://github.com/ASDWQad/FuckFpm
标签:#渗透测试
更新了:渗透测试
描述:渗透测试中针对Php Disable_functions的Fpm利用
URL:https://github.com/ASDWQad/FuckFpm
标签:#渗透测试
GitHub监控消息提醒!!!
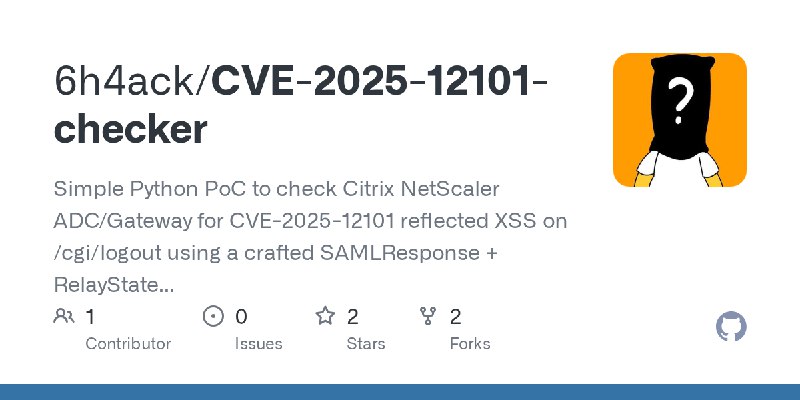
更新了:CVE-2025
描述:Simple Python PoC to check Citrix NetScaler ADC/Gateway for CVE-2025-12101 reflected XSS on /cgi/logout using a crafted SAMLResponse + RelayState payload
URL:https://github.com/6h4ack/CVE-2025-12101-checker
标签:#CVE-2025
更新了:CVE-2025
描述:Simple Python PoC to check Citrix NetScaler ADC/Gateway for CVE-2025-12101 reflected XSS on /cgi/logout using a crafted SAMLResponse + RelayState payload
URL:https://github.com/6h4ack/CVE-2025-12101-checker
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:The public exploit for CVE-2025-13027
URL:https://github.com/yourluckyday3-art/CVE-2025-13027-Exploit
标签:#CVE-2025
更新了:CVE-2025
描述:The public exploit for CVE-2025-13027
URL:https://github.com/yourluckyday3-art/CVE-2025-13027-Exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:Red Team
描述:🔒 Automate cybersecurity tasks with n8n workflows for Red Team, Blue Team, and Application Security, enhancing efficiency and response times.
URL:https://github.com/Aditya-Sec/ReconVeritas-Automated-Recon-Tool
标签:#Red Team
更新了:Red Team
描述:🔒 Automate cybersecurity tasks with n8n workflows for Red Team, Blue Team, and Application Security, enhancing efficiency and response times.
URL:https://github.com/Aditya-Sec/ReconVeritas-Automated-Recon-Tool
标签:#Red Team
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-31133 PoC
URL:https://github.com/skynet-f-nvidia/CVE-2025-31133
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-31133 PoC
URL:https://github.com/skynet-f-nvidia/CVE-2025-31133
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:免杀
描述:平台:Windows/Mac/Linux。脚本语言:多种、不限;我流,按需编写。涉及:桌面基线排查、软件激活破解、免杀及特权执行、渗透式支援固件识别读写、主机账户密码空值检测、Wi-Fi密码扫描、云主机终端安全加固、主机系统日志分析、自然语言处理、人文社科信息数据分析等。
URL:https://github.com/ddlmanus/jcly-shop
标签:#免杀
更新了:免杀
描述:平台:Windows/Mac/Linux。脚本语言:多种、不限;我流,按需编写。涉及:桌面基线排查、软件激活破解、免杀及特权执行、渗透式支援固件识别读写、主机账户密码空值检测、Wi-Fi密码扫描、云主机终端安全加固、主机系统日志分析、自然语言处理、人文社科信息数据分析等。
URL:https://github.com/ddlmanus/jcly-shop
标签:#免杀
GitHub监控消息提醒!!!
更新了:RCE
描述:SUKUNA v11.0 – Multi-language penetration testing tool (Python + C + Assembly). Features OWASP Top 10 scanning, RCE proof, WAF bypass, and GUI/CLI interface. Author: @canmitm
URL:https://github.com/root-flow/sukuna
标签:#RCE
更新了:RCE
描述:SUKUNA v11.0 – Multi-language penetration testing tool (Python + C + Assembly). Features OWASP Top 10 scanning, RCE proof, WAF bypass, and GUI/CLI interface. Author: @canmitm
URL:https://github.com/root-flow/sukuna
标签:#RCE
GitHub监控消息提醒!!!
更新了:渗透测试
描述:一个基于langchain4j开发的ai辅助渗透测试助手
URL:https://github.com/gtasb/Burp-AI-Analyzer
标签:#渗透测试
更新了:渗透测试
描述:一个基于langchain4j开发的ai辅助渗透测试助手
URL:https://github.com/gtasb/Burp-AI-Analyzer
标签:#渗透测试
GitHub监控消息提醒!!!
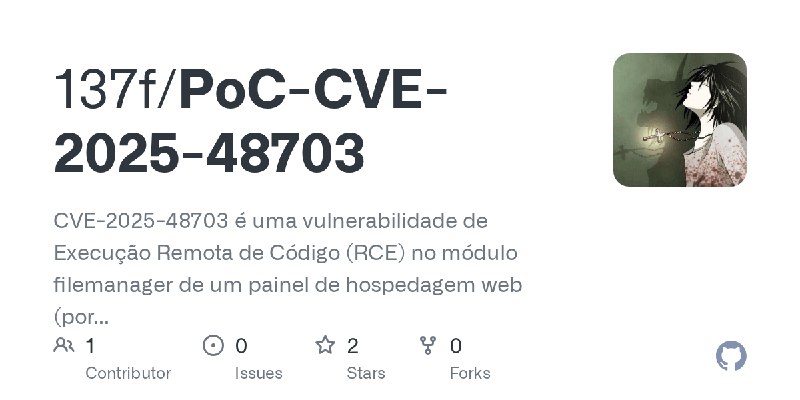
更新了:CVE-2025
描述:Exploit and test stand for CVE-2025-2945
URL:https://github.com/137f/PoC-CVE-2025-48703
标签:#CVE-2025
更新了:CVE-2025
描述:Exploit and test stand for CVE-2025-2945
URL:https://github.com/137f/PoC-CVE-2025-48703
标签:#CVE-2025
GitHub监控消息提醒!!!
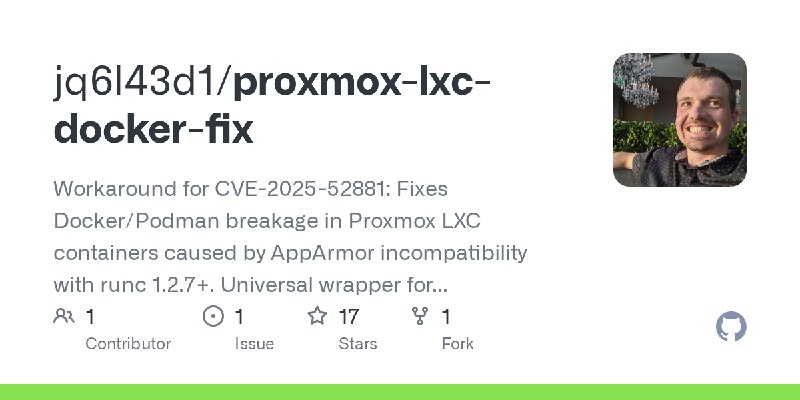
更新了:CVE-2025
描述:🔍 Demonstrate the CVE-2025-32463 privilege-escalation flaw in sudo's chroot feature with this minimal, reproducible proof of concept environment.
URL:https://github.com/jq6l43d1/proxmox-lxc-docker-fix
标签:#CVE-2025
更新了:CVE-2025
描述:🔍 Demonstrate the CVE-2025-32463 privilege-escalation flaw in sudo's chroot feature with this minimal, reproducible proof of concept environment.
URL:https://github.com/jq6l43d1/proxmox-lxc-docker-fix
标签:#CVE-2025
GitHub监控消息提醒!!!
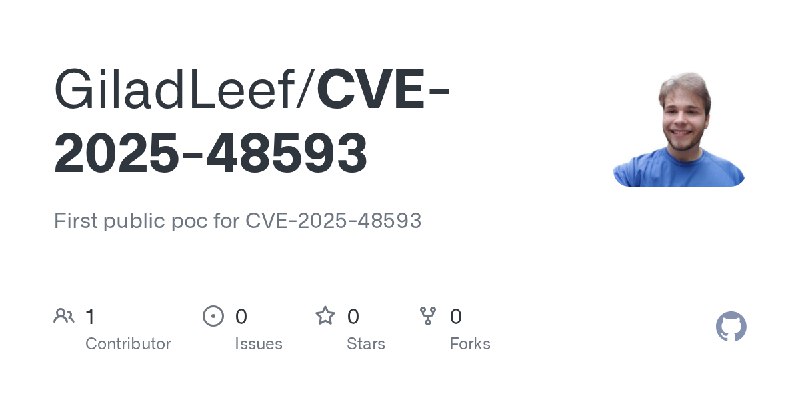
更新了:CVE-2025
描述:First public poc for CVE-2025-48593
URL:https://github.com/GiladLeef/CVE-2025-48593
标签:#CVE-2025
更新了:CVE-2025
描述:First public poc for CVE-2025-48593
URL:https://github.com/GiladLeef/CVE-2025-48593
标签:#CVE-2025
GitHub监控消息提醒!!!
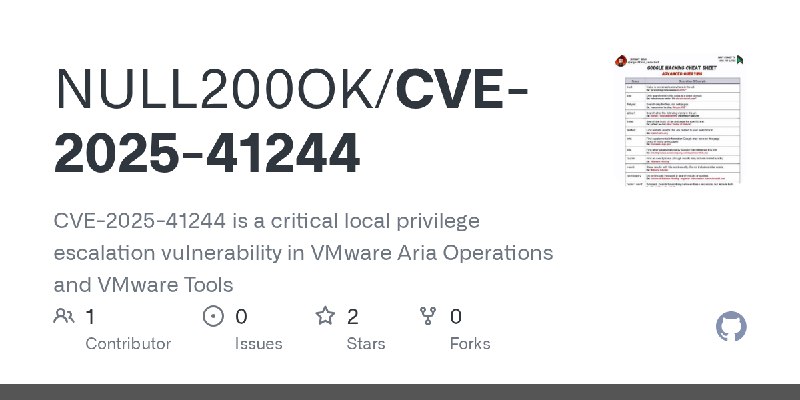
更新了:CVE-2025
描述:CVE-2025-41244 is a critical local privilege escalation vulnerability in VMware Aria Operations and VMware Tools
URL:https://github.com/IBO-ATTACKS/CVE-2025-41244
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-41244 is a critical local privilege escalation vulnerability in VMware Aria Operations and VMware Tools
URL:https://github.com/IBO-ATTACKS/CVE-2025-41244
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:POC CVE-2025-9223
URL:https://github.com/networkkiller/CVE-2025-9223
标签:#CVE-2025
更新了:CVE-2025
描述:POC CVE-2025-9223
URL:https://github.com/networkkiller/CVE-2025-9223
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:Cobalt Strike
描述:A BOF implementation of curl for Cobalt Strike - HTTP/HTTPS client with TLS certificate inspection
URL:https://github.com/chryzsh/curl-bof
标签:#Cobalt Strike
更新了:Cobalt Strike
描述:A BOF implementation of curl for Cobalt Strike - HTTP/HTTPS client with TLS certificate inspection
URL:https://github.com/chryzsh/curl-bof
标签:#Cobalt Strike
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:AstrBot老版本RCE
URL:https://github.com/Marven11/CVE-2025-55449-AstrBot-RCE
标签:#CVE-2025
更新了:CVE-2025
描述:AstrBot老版本RCE
URL:https://github.com/Marven11/CVE-2025-55449-AstrBot-RCE
标签:#CVE-2025