监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
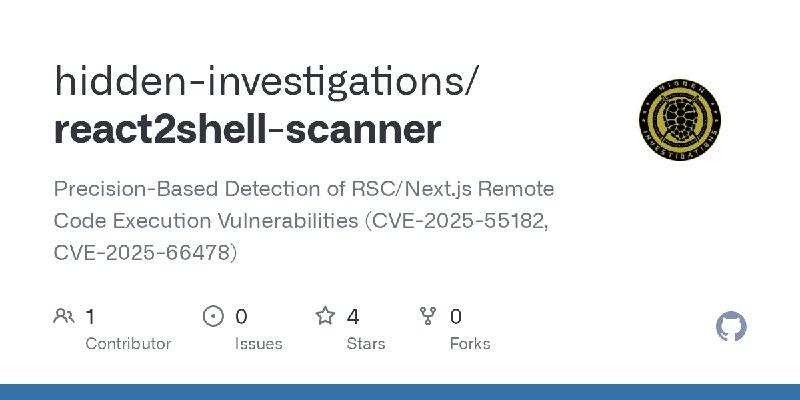
更新了:CVE-2025
描述:Precision-Based Detection of RSC/Next.js Remote Code Execution Vulnerabilities (CVE-2025-55182, CVE-2025-66478)
URL:https://github.com/hidden-investigations/react2shell-scanner
标签:#CVE-2025
更新了:CVE-2025
描述:Precision-Based Detection of RSC/Next.js Remote Code Execution Vulnerabilities (CVE-2025-55182, CVE-2025-66478)
URL:https://github.com/hidden-investigations/react2shell-scanner
标签:#CVE-2025
GitHub监控消息提醒!!!
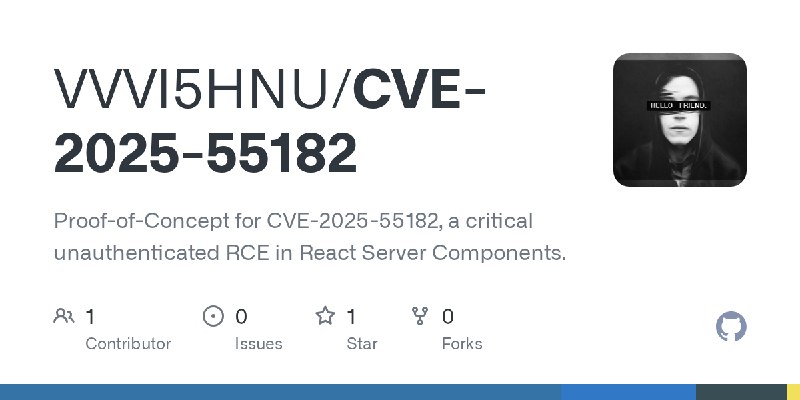
更新了:CVE-2025
描述:Proof-of-Concept for CVE-2025-55182, a critical unauthenticated RCE in React Server Components.
URL:https://github.com/VVVI5HNU/CVE-2025-55182
标签:#CVE-2025
更新了:CVE-2025
描述:Proof-of-Concept for CVE-2025-55182, a critical unauthenticated RCE in React Server Components.
URL:https://github.com/VVVI5HNU/CVE-2025-55182
标签:#CVE-2025
GitHub监控消息提醒!!!
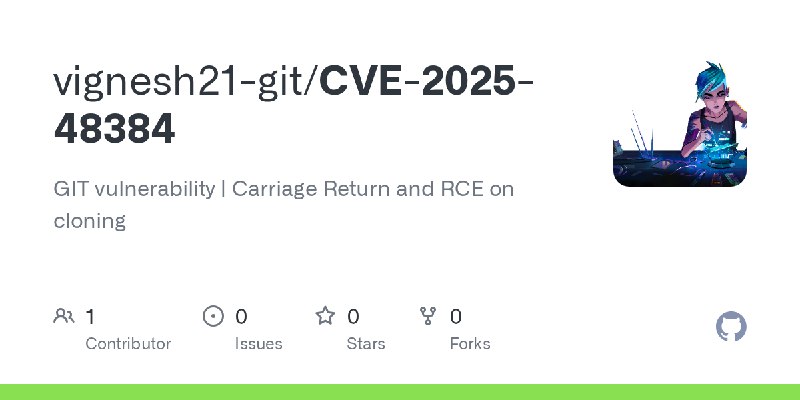
更新了:RCE
描述:GIT vulnerability | Carriage Return and RCE on cloning
URL:https://github.com/vignesh21-git/CVE-2025-48384
标签:#RCE
更新了:RCE
描述:GIT vulnerability | Carriage Return and RCE on cloning
URL:https://github.com/vignesh21-git/CVE-2025-48384
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:a critical Remote Code Execution (RCE) vulnerability in React Server Components (RSC). It also includes a realistic \"Lab Environment\" to safely test and understand the vulnerability.
URL:https://github.com/BimBoxH4/CVE-2025-66039_CVE-2025-61675_CVE-2025-61678_reePBX
标签:#CVE-2025
更新了:CVE-2025
描述:a critical Remote Code Execution (RCE) vulnerability in React Server Components (RSC). It also includes a realistic \"Lab Environment\" to safely test and understand the vulnerability.
URL:https://github.com/BimBoxH4/CVE-2025-66039_CVE-2025-61675_CVE-2025-61678_reePBX
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:💥Extension Tool para Auditoría y Explotación avanzada RCE/Source Leak/Dos (CVE-2025-55182/83/84) para entornos Next.js y React Server Components (RSC) directamente desde tu navegador ❌
URL:https://github.com/MammaniNelsonD/React2P4IM0Nshell
标签:#RCE
更新了:RCE
描述:💥Extension Tool para Auditoría y Explotación avanzada RCE/Source Leak/Dos (CVE-2025-55182/83/84) para entornos Next.js y React Server Components (RSC) directamente desde tu navegador ❌
URL:https://github.com/MammaniNelsonD/React2P4IM0Nshell
标签:#RCE
GitHub监控消息提醒!!!
更新了:代码审计
描述:开源的代码审计平台 - 支持项目级/文件级/片段级审计,支持 10+ LLM、自定义规则集(内置OWASP Top 10 规则集)、自定义提示词模板、可解释分析、PDF 报告导出。支持ollama私有部署模型,代码可不出内网。
URL:https://github.com/shus-s/javaweb-Study-Room-Reservation-System
标签:#代码审计
更新了:代码审计
描述:开源的代码审计平台 - 支持项目级/文件级/片段级审计,支持 10+ LLM、自定义规则集(内置OWASP Top 10 规则集)、自定义提示词模板、可解释分析、PDF 报告导出。支持ollama私有部署模型,代码可不出内网。
URL:https://github.com/shus-s/javaweb-Study-Room-Reservation-System
标签:#代码审计
GitHub监控消息提醒!!!
更新了:代码审计
描述:开源的代码审计平台 - 支持项目级/文件级/片段级审计,支持 10+ LLM、自定义规则集(内置OWASP Top 10 规则集)、自定义提示词模板、可解释分析、PDF 报告导出。支持ollama私有部署模型,代码可不出内网。
URL:https://github.com/shus-s/java-web-
标签:#代码审计
更新了:代码审计
描述:开源的代码审计平台 - 支持项目级/文件级/片段级审计,支持 10+ LLM、自定义规则集(内置OWASP Top 10 规则集)、自定义提示词模板、可解释分析、PDF 报告导出。支持ollama私有部署模型,代码可不出内网。
URL:https://github.com/shus-s/java-web-
标签:#代码审计
GitHub监控消息提醒!!!
更新了:RCE
描述:TCP/UDP server & client, potential file transfer program, maybe RCE or Trojan malware
URL:https://github.com/win4er/messenger
标签:#RCE
更新了:RCE
描述:TCP/UDP server & client, potential file transfer program, maybe RCE or Trojan malware
URL:https://github.com/win4er/messenger
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Check if your server is affected by CVE-2025-55182 & CVE-2025-66478
URL:https://github.com/mounta11n/CHECK-CVE-2025-55182-AND-CVE-2025-66478
标签:#CVE-2025
更新了:CVE-2025
描述:Check if your server is affected by CVE-2025-55182 & CVE-2025-66478
URL:https://github.com/mounta11n/CHECK-CVE-2025-55182-AND-CVE-2025-66478
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Python script for Testing CVE-2025-55184
URL:https://github.com/Kajal5414/CVE-2025-55184_Testing
标签:#CVE-2025
更新了:CVE-2025
描述:Python script for Testing CVE-2025-55184
URL:https://github.com/Kajal5414/CVE-2025-55184_Testing
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🔧 Exploit CVE-2025-33073 with this universal tool for Windows Domain Controllers, enabling SYSTEM-level code execution through automated techniques.
URL:https://github.com/cyberleelawat/CVE-2025-55184
标签:#CVE-2025
更新了:CVE-2025
描述:🔧 Exploit CVE-2025-33073 with this universal tool for Windows Domain Controllers, enabling SYSTEM-level code execution through automated techniques.
URL:https://github.com/cyberleelawat/CVE-2025-55184
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:A hybrid security scanner for detecting CVE-2025-55182 in Next.js and Waku applications. Features combined static code analysis and safe dynamic verification for DevSecOps workflows.
URL:https://github.com/TrixSec/CVE-2025-55182-Scanner
标签:#CVE-2025
更新了:CVE-2025
描述:A hybrid security scanner for detecting CVE-2025-55182 in Next.js and Waku applications. Features combined static code analysis and safe dynamic verification for DevSecOps workflows.
URL:https://github.com/TrixSec/CVE-2025-55182-Scanner
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:NodeJS-based exploit script and scanner for the React Server Components \"React2Shell\" vulnerability (CVE-2025-55182).
URL:https://github.com/sangleshubham/React-Security-CVE-2025-55182-Exploit
标签:#CVE-2025
更新了:CVE-2025
描述:NodeJS-based exploit script and scanner for the React Server Components \"React2Shell\" vulnerability (CVE-2025-55182).
URL:https://github.com/sangleshubham/React-Security-CVE-2025-55182-Exploit
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:PoC for Microsoft Amplifier CLI RCE vulnerability via malicious project configuration
URL:https://github.com/nebariai/MicrosoftAmplifierPoC
标签:#RCE
更新了:RCE
描述:PoC for Microsoft Amplifier CLI RCE vulnerability via malicious project configuration
URL:https://github.com/nebariai/MicrosoftAmplifierPoC
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:High-performance Go implementation for detecting React Server Components RCE vulnerabilities (CVE-2025-55182 & CVE-2025-66478).
URL:https://github.com/h0tak88r/next88
标签:#RCE
更新了:RCE
描述:High-performance Go implementation for detecting React Server Components RCE vulnerabilities (CVE-2025-55182 & CVE-2025-66478).
URL:https://github.com/h0tak88r/next88
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:A hands-on lab for understanding and exploiting CVE-2025-55182 (React2Shell) - Remote Code Execution in React Server Components
URL:https://github.com/dhananjayakumarn/CVE-2025-55182-Lab
标签:#CVE-2025
更新了:CVE-2025
描述:A hands-on lab for understanding and exploiting CVE-2025-55182 (React2Shell) - Remote Code Execution in React Server Components
URL:https://github.com/dhananjayakumarn/CVE-2025-55182-Lab
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:A research report on CVE-2025-55182 (React2Shell).
URL:https://github.com/Kugelbyte/React2Shell-Analysis
标签:#CVE-2025
更新了:CVE-2025
描述:A research report on CVE-2025-55182 (React2Shell).
URL:https://github.com/Kugelbyte/React2Shell-Analysis
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:A CVE-2025-55182(React2Shell) Toolbox Application
URL:https://github.com/MoLeft/React2Shell-Toolbox
标签:#CVE-2025
更新了:CVE-2025
描述:A CVE-2025-55182(React2Shell) Toolbox Application
URL:https://github.com/MoLeft/React2Shell-Toolbox
标签:#CVE-2025