监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Disclosure for CVE-2025-9886 and CVE-2025-9952
URL:https://github.com/MooseLoveti/Trinity-Audio-CVE-Report2
标签:#CVE-2025
更新了:CVE-2025
描述:Disclosure for CVE-2025-9886 and CVE-2025-9952
URL:https://github.com/MooseLoveti/Trinity-Audio-CVE-Report2
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:信息收集
描述:Scout 是一个基于 Roo Code VS Code 扩展 设计的实验性 Agent 实现。它专注于通过模拟人类行为进行精准的网络信息收集、研究与交互,旨在将 Roo Code 转变为一个强大的 Web 研究助手。
URL:https://github.com/small-bears/enterprise
标签:#信息收集
更新了:信息收集
描述:Scout 是一个基于 Roo Code VS Code 扩展 设计的实验性 Agent 实现。它专注于通过模拟人类行为进行精准的网络信息收集、研究与交互,旨在将 Roo Code 转变为一个强大的 Web 研究助手。
URL:https://github.com/small-bears/enterprise
标签:#信息收集
GitHub监控消息提醒!!!
更新了:RCE
描述:Smart RCE Hackathon 2026 - Web Platform
URL:https://github.com/DrTMUSHACoder/Smart-RCE-Hackathon-2026-Website
标签:#RCE
更新了:RCE
描述:Smart RCE Hackathon 2026 - Web Platform
URL:https://github.com/DrTMUSHACoder/Smart-RCE-Hackathon-2026-Website
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/vedantkulkarni1234/AURORA
标签:#RCE
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/vedantkulkarni1234/AURORA
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:ZipSlip RCE (Authenticated) in PluckCMS 4.7.20
URL:https://github.com/RajChowdhury240/CVE-2025-67435
标签:#CVE-2025
更新了:CVE-2025
描述:ZipSlip RCE (Authenticated) in PluckCMS 4.7.20
URL:https://github.com/RajChowdhury240/CVE-2025-67435
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:CVE-2025-55182 React2Shell PoC - RCE via React Server Components
URL:https://github.com/p3ta00/react2shell-poc
标签:#RCE
更新了:RCE
描述:CVE-2025-55182 React2Shell PoC - RCE via React Server Components
URL:https://github.com/p3ta00/react2shell-poc
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Contact Form Injection -> RCE -> Account Take Over
URL:https://github.com/Abenezer-A/Abenezer_Alemayehu_AXUMxINSA_Challenge
标签:#RCE
更新了:RCE
描述:Contact Form Injection -> RCE -> Account Take Over
URL:https://github.com/Abenezer-A/Abenezer_Alemayehu_AXUMxINSA_Challenge
标签:#RCE
GitHub监控消息提醒!!!
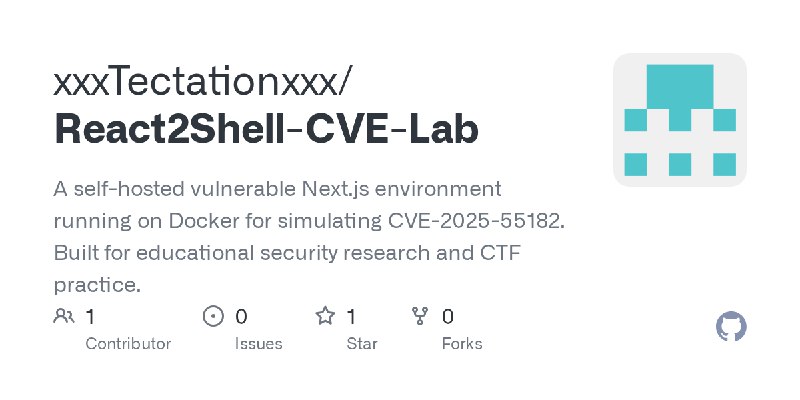
更新了:CVE-2025
描述:A self-hosted vulnerable Next.js environment running on Docker for simulating CVE-2025-55182. Built for educational security research and CTF practice.
URL:https://github.com/xxxTectationxxx/React2Shell-CVE-Lab
标签:#CVE-2025
更新了:CVE-2025
描述:A self-hosted vulnerable Next.js environment running on Docker for simulating CVE-2025-55182. Built for educational security research and CTF practice.
URL:https://github.com/xxxTectationxxx/React2Shell-CVE-Lab
标签:#CVE-2025
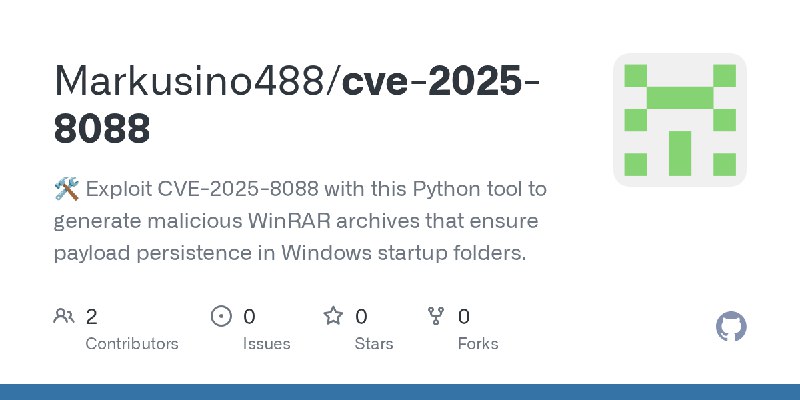
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🛠 Exploit CVE-2025-8088 with this Python tool to generate malicious WinRAR archives that ensure payload persistence in Windows startup folders.
URL:https://github.com/Markusino488/cve-2025-8088
标签:#CVE-2025
更新了:CVE-2025
描述:🛠 Exploit CVE-2025-8088 with this Python tool to generate malicious WinRAR archives that ensure payload persistence in Windows startup folders.
URL:https://github.com/Markusino488/cve-2025-8088
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:Interactive RCE Pseudo-Shell Tool
URL:https://github.com/danielorlando97/iwshell
标签:#RCE
更新了:RCE
描述:Interactive RCE Pseudo-Shell Tool
URL:https://github.com/danielorlando97/iwshell
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Interactive RCE Pseudo-Shell Tool
URL:https://github.com/messyhick3-tech/WinX-DVD-Ripper-6.8.4-MacOSX
标签:#RCE
更新了:RCE
描述:Interactive RCE Pseudo-Shell Tool
URL:https://github.com/messyhick3-tech/WinX-DVD-Ripper-6.8.4-MacOSX
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Contact Form Injection -> RCE -> Account Take Over
URL:https://github.com/Abenezer-A/Project-11---Contact-Form-Injection
标签:#RCE
更新了:RCE
描述:Contact Form Injection -> RCE -> Account Take Over
URL:https://github.com/Abenezer-A/Project-11---Contact-Form-Injection
标签:#RCE
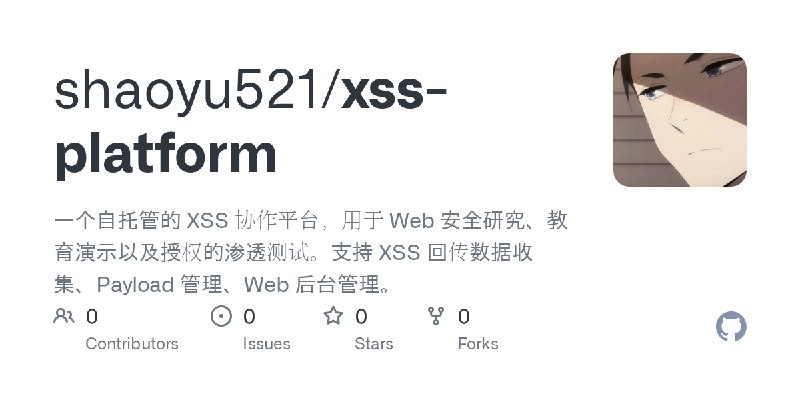
GitHub监控消息提醒!!!
更新了:渗透测试
描述:一个自托管的 XSS 协作平台,用于 Web 安全研究、教育演示以及授权的渗透测试。支持 XSS 回传数据收集、Payload 管理、Web 后台管理。
URL:https://github.com/shaoyu521/xss-platform
标签:#渗透测试
更新了:渗透测试
描述:一个自托管的 XSS 协作平台,用于 Web 安全研究、教育演示以及授权的渗透测试。支持 XSS 回传数据收集、Payload 管理、Web 后台管理。
URL:https://github.com/shaoyu521/xss-platform
标签:#渗透测试
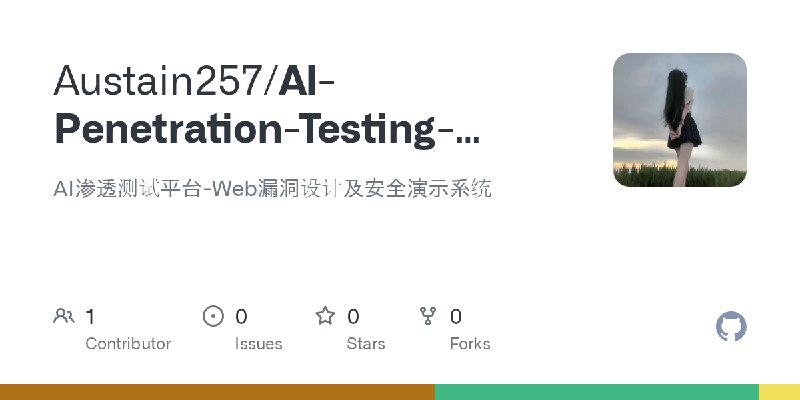
GitHub监控消息提醒!!!
更新了:渗透测试
描述:AI渗透测试平台-Web漏洞设计及安全演示系统
URL:https://github.com/Austain257/AI-Penetration-Testing-Platform
标签:#渗透测试
更新了:渗透测试
描述:AI渗透测试平台-Web漏洞设计及安全演示系统
URL:https://github.com/Austain257/AI-Penetration-Testing-Platform
标签:#渗透测试
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:writeups for (CVE-2025-67586, CVE-2025-67985, CVE-2025-67986)
URL:https://github.com/r0xtsec/CVE
标签:#CVE-2025
更新了:CVE-2025
描述:writeups for (CVE-2025-67586, CVE-2025-67985, CVE-2025-67986)
URL:https://github.com/r0xtsec/CVE
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:CTF de Seguridad en Bases de Datos (URJC): retos SQL Injection, blind/time-based, RCE con INTO OUTFILE
URL:https://github.com/juansrz/dbsec-P2-ctf
标签:#RCE
更新了:RCE
描述:CTF de Seguridad en Bases de Datos (URJC): retos SQL Injection, blind/time-based, RCE con INTO OUTFILE
URL:https://github.com/juansrz/dbsec-P2-ctf
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🔍 Demonstrate and validate the `addressof` and `fakeobj` primitives in the V8 sandbox for advanced security research on CVE-2025-6554.
URL:https://github.com/MeGaNeKoS/secure-by-default-rce-demo
标签:#CVE-2025
更新了:CVE-2025
描述:🔍 Demonstrate and validate the `addressof` and `fakeobj` primitives in the V8 sandbox for advanced security research on CVE-2025-6554.
URL:https://github.com/MeGaNeKoS/secure-by-default-rce-demo
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Here is the CVE-2025-65817
URL:https://github.com/Istaarkk/CVE-2025-65817
标签:#CVE-2025
更新了:CVE-2025
描述:Here is the CVE-2025-65817
URL:https://github.com/Istaarkk/CVE-2025-65817
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:OpsGuard eliminates the \"3 AM PagerDuty\" nightmare, specifically protecting against threats like the recent CVE-2025-55184 (Next.js DoS)
URL:https://github.com/shubham-01-star/OpsGuard-simulation
标签:#CVE-2025
更新了:CVE-2025
描述:OpsGuard eliminates the \"3 AM PagerDuty\" nightmare, specifically protecting against threats like the recent CVE-2025-55184 (Next.js DoS)
URL:https://github.com/shubham-01-star/OpsGuard-simulation
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:🔍 Demonstrate and validate the `addressof` and `fakeobj` primitives in the V8 sandbox for advanced security research on CVE-2025-6554.
URL:https://github.com/mahaveer-choudhary/CVE-2025-55182
标签:#CVE-2025
更新了:CVE-2025
描述:🔍 Demonstrate and validate the `addressof` and `fakeobj` primitives in the V8 sandbox for advanced security research on CVE-2025-6554.
URL:https://github.com/mahaveer-choudhary/CVE-2025-55182
标签:#CVE-2025