监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
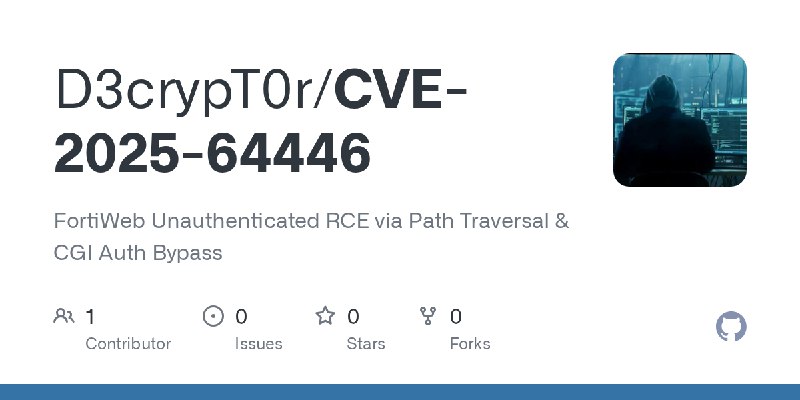
更新了:RCE
描述:FortiWeb Unauthenticated RCE via Path Traversal & CGI Auth Bypass
URL:https://github.com/D3crypT0r/CVE-2025-64446
标签:#RCE
更新了:RCE
描述:FortiWeb Unauthenticated RCE via Path Traversal & CGI Auth Bypass
URL:https://github.com/D3crypT0r/CVE-2025-64446
标签:#RCE
GitHub监控消息提醒!!!
更新了:内网渗透
描述:GYscan是一款基于Go语言开发的现代化内网横向渗透测试工具,专为安全研究人员、渗透测试工程师和红队成员设计。项目采用模块化架构,包含C2服务器端和客户端组件,支持Windows和Linux平台,提供系统安全分析和漏洞扫描功能。
URL:https://github.com/Puremilk-SYC/PuremilkJS
标签:#内网渗透
更新了:内网渗透
描述:GYscan是一款基于Go语言开发的现代化内网横向渗透测试工具,专为安全研究人员、渗透测试工程师和红队成员设计。项目采用模块化架构,包含C2服务器端和客户端组件,支持Windows和Linux平台,提供系统安全分析和漏洞扫描功能。
URL:https://github.com/Puremilk-SYC/PuremilkJS
标签:#内网渗透
GitHub监控消息提醒!!!
更新了:RCE
描述:merge malicious pdf xlsx docs svg etc Generates all possible payloads for SSRF, XXE, RCE, XSS, Path Traversal, NTLM Leak, LFI, and other vulnerabilities in all common file formats
URL:https://github.com/karthickkumar3011/DVWA-Penetration-Testing-Report
标签:#RCE
更新了:RCE
描述:merge malicious pdf xlsx docs svg etc Generates all possible payloads for SSRF, XXE, RCE, XSS, Path Traversal, NTLM Leak, LFI, and other vulnerabilities in all common file formats
URL:https://github.com/karthickkumar3011/DVWA-Penetration-Testing-Report
标签:#RCE
GitHub监控消息提醒!!!
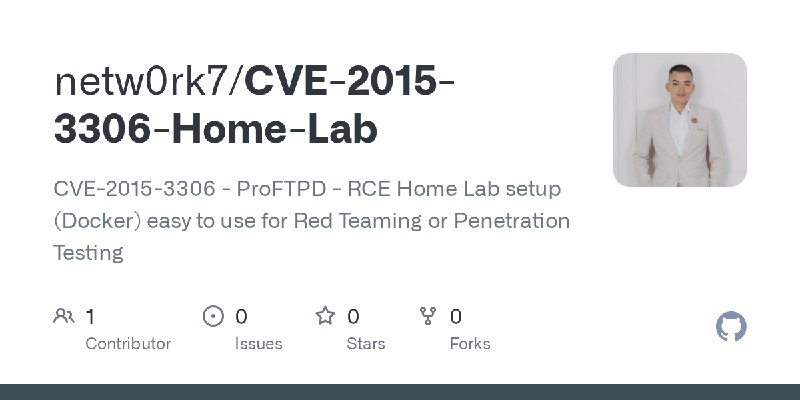
更新了:RCE
描述:CVE-2015-3306 - ProFTPD - RCE Home Lab setup (Docker) easy to use for Red Teaming or Penetration Testing
URL:https://github.com/netw0rk7/CVE-2015-3306-Home-Lab
标签:#RCE
更新了:RCE
描述:CVE-2015-3306 - ProFTPD - RCE Home Lab setup (Docker) easy to use for Red Teaming or Penetration Testing
URL:https://github.com/netw0rk7/CVE-2015-3306-Home-Lab
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:A scanner for the FortiNet vulnerability CVE-2025-64446
URL:https://github.com/sensepost/CVE-2025-64446
标签:#CVE-2025
更新了:CVE-2025
描述:A scanner for the FortiNet vulnerability CVE-2025-64446
URL:https://github.com/sensepost/CVE-2025-64446
标签:#CVE-2025
GitHub监控消息提醒!!!
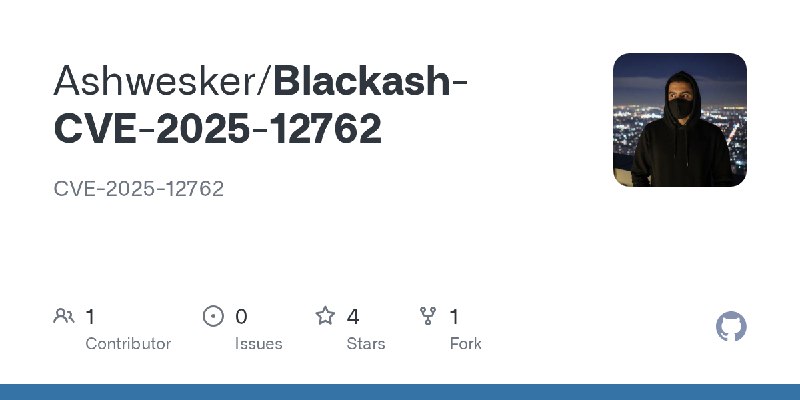
更新了:CVE-2025
描述:CVE-2025-12762
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-12762
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-12762
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-12762
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:RCE
描述:merge malicious pdf xlsx docs svg etc Generates all possible payloads for SSRF, XXE, RCE, XSS, Path Traversal, NTLM Leak, LFI, and other vulnerabilities in all common file formats
URL:https://github.com/niranc/UploadRenderAllTheThings
标签:#RCE
更新了:RCE
描述:merge malicious pdf xlsx docs svg etc Generates all possible payloads for SSRF, XXE, RCE, XSS, Path Traversal, NTLM Leak, LFI, and other vulnerabilities in all common file formats
URL:https://github.com/niranc/UploadRenderAllTheThings
标签:#RCE
GitHub监控消息提醒!!!
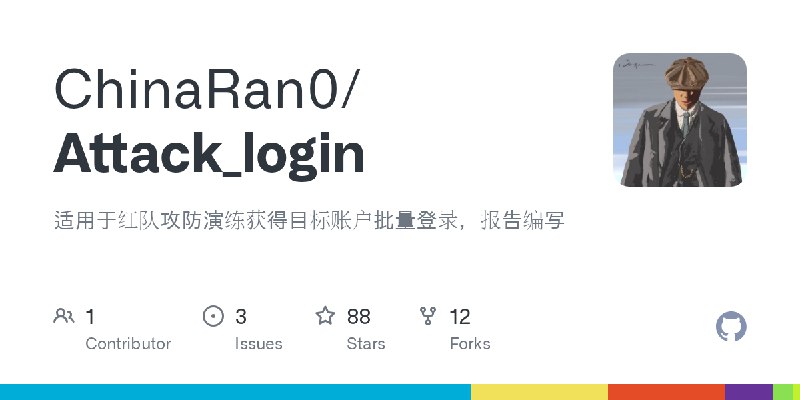
更新了:红队
描述:适用于红队攻防演练获得目标账户批量登录,报告编写
URL:https://github.com/ChinaRan0/Attack_login
标签:#红队
更新了:红队
描述:适用于红队攻防演练获得目标账户批量登录,报告编写
URL:https://github.com/ChinaRan0/Attack_login
标签:#红队
GitHub监控消息提醒!!!
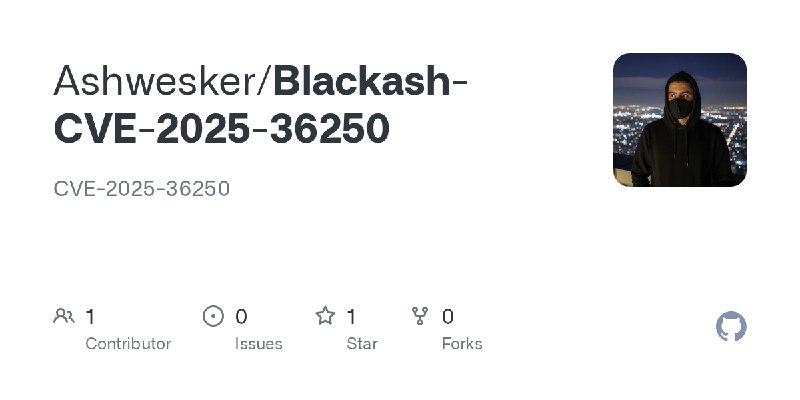
更新了:CVE-2025
描述:CVE-2025-36250
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-36250
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-36250
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-36250
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:免杀
描述:ModifyNeo-reGeorg 是一款基于 Neo-reGeorg 深度重构的高性能正向代理工具,采用 HTTP 隧道实现流量封装,天然具备强伪装与免杀优势,一键生成php、jsp、asp等8种模板文件。目前测试可过火绒、360、defender、天擎、绿盟EDR。
URL:https://github.com/6yx1n0930-art/ModifyNeo-reGeorg-V1.0
标签:#免杀
更新了:免杀
描述:ModifyNeo-reGeorg 是一款基于 Neo-reGeorg 深度重构的高性能正向代理工具,采用 HTTP 隧道实现流量封装,天然具备强伪装与免杀优势,一键生成php、jsp、asp等8种模板文件。目前测试可过火绒、360、defender、天擎、绿盟EDR。
URL:https://github.com/6yx1n0930-art/ModifyNeo-reGeorg-V1.0
标签:#免杀
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Hands-on exploitation lab for Roundcube Webmail CVE-2025-49113 (authenticated PHP object deserialization → RCE) to read /secret.txt.
URL:https://github.com/demining/Scalar-Venom-Attack
标签:#CVE-2025
更新了:CVE-2025
描述:Hands-on exploitation lab for Roundcube Webmail CVE-2025-49113 (authenticated PHP object deserialization → RCE) to read /secret.txt.
URL:https://github.com/demining/Scalar-Venom-Attack
标签:#CVE-2025
GitHub监控消息提醒!!!
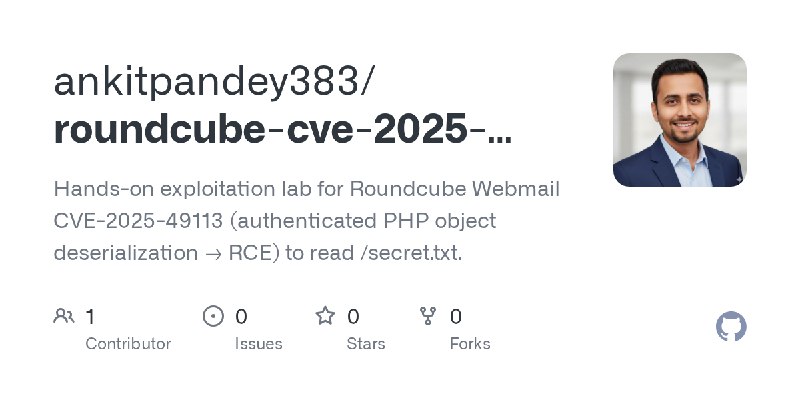
更新了:CVE-2025
描述:Hands-on exploitation lab for Roundcube Webmail CVE-2025-49113 (authenticated PHP object deserialization → RCE) to read /secret.txt.
URL:https://github.com/ankitpandey383/roundcube-cve-2025-49113-lab
标签:#CVE-2025
更新了:CVE-2025
描述:Hands-on exploitation lab for Roundcube Webmail CVE-2025-49113 (authenticated PHP object deserialization → RCE) to read /secret.txt.
URL:https://github.com/ankitpandey383/roundcube-cve-2025-49113-lab
标签:#CVE-2025
GitHub监控消息提醒!!!
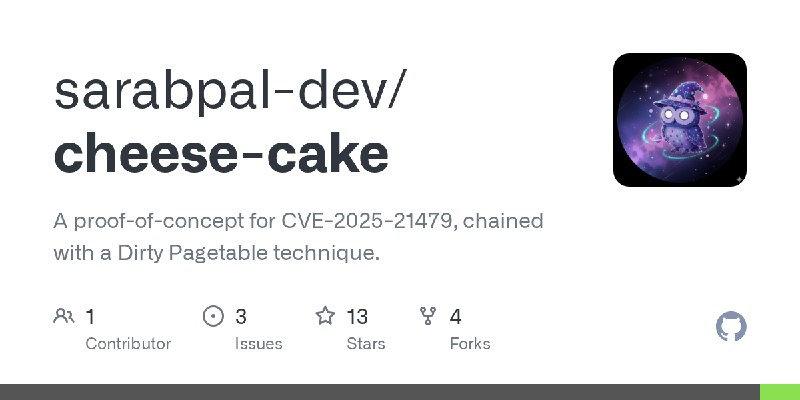
更新了:CVE-2025
描述:A proof-of-concept for CVE-2025-21479, chained with a Dirty Pagetable technique.
URL:https://github.com/sarabpal-dev/cheese-cake
标签:#CVE-2025
更新了:CVE-2025
描述:A proof-of-concept for CVE-2025-21479, chained with a Dirty Pagetable technique.
URL:https://github.com/sarabpal-dev/cheese-cake
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-10720 PoC
URL:https://github.com/lorenzocamilli/CVE-2025-62950-PoC
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-10720 PoC
URL:https://github.com/lorenzocamilli/CVE-2025-62950-PoC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:CVE-2025-64484
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-64484
标签:#CVE-2025
更新了:CVE-2025
描述:CVE-2025-64484
URL:https://github.com/B1ack4sh/Blackash-CVE-2025-64484
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:placeholder for CitrixBleed 2.0 CVE-2025-5777
URL:https://github.com/mr-r3b00t/CVE-2025-5777
标签:#CVE-2025
更新了:CVE-2025
描述:placeholder for CitrixBleed 2.0 CVE-2025-5777
URL:https://github.com/mr-r3b00t/CVE-2025-5777
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:Unauthenticated RCE PoC in Microsoft Windows Server Update Service (WSUS) - CVE-2025-59287 & CVE-2023-35317
URL:https://github.com/M507/CVE-2025-59287-PoC
标签:#CVE-2025
更新了:CVE-2025
描述:Unauthenticated RCE PoC in Microsoft Windows Server Update Service (WSUS) - CVE-2025-59287 & CVE-2023-35317
URL:https://github.com/M507/CVE-2025-59287-PoC
标签:#CVE-2025
GitHub监控消息提醒!!!
更新了:CVE-2025
描述:maybe a poc for CVE-2025-40019
URL:https://github.com/guard-wait/CVE-2025-40019_POC
标签:#CVE-2025
更新了:CVE-2025
描述:maybe a poc for CVE-2025-40019
URL:https://github.com/guard-wait/CVE-2025-40019_POC
标签:#CVE-2025