监控Github上的漏洞、红队等信息。
GitHub监控消息提醒!!!
更新了:漏洞验证
描述:渗透测试与 CTF 攻防相关的 Python 脚本集合,包含 Web 漏洞 POC、编码绕过工具、数据处理脚本等,用于实战场景中的漏洞验证与辅助测试。
URL:https://github.com/bfdfhdsfdd-crypto/CVE-2026-22444
标签:#漏洞验证
更新了:漏洞验证
描述:渗透测试与 CTF 攻防相关的 Python 脚本集合,包含 Web 漏洞 POC、编码绕过工具、数据处理脚本等,用于实战场景中的漏洞验证与辅助测试。
URL:https://github.com/bfdfhdsfdd-crypto/CVE-2026-22444
标签:#漏洞验证
GitHub监控消息提醒!!!
更新了:漏洞检测
描述:CVE-2026-24061 漏洞检测工具
URL:https://github.com/monstertsl/CVE-2026-24061
标签:#漏洞检测
更新了:漏洞检测
描述:CVE-2026-24061 漏洞检测工具
URL:https://github.com/monstertsl/CVE-2026-24061
标签:#漏洞检测
GitHub监控消息提醒!!!
更新了:钓鱼
描述:跨平台钓鱼防护工具,检测并隔离CamPhish等恶意工具
URL:https://github.com/Admintt73/PhishingGuard
标签:#钓鱼
更新了:钓鱼
描述:跨平台钓鱼防护工具,检测并隔离CamPhish等恶意工具
URL:https://github.com/Admintt73/PhishingGuard
标签:#钓鱼
GitHub监控消息提醒!!!
更新了:Red Team
描述:AI Security Platform: Defense (217 engines) + Offense (39K+ payloads) | RLM-Toolkit: LangChain alternative with infinite context | OWASP LLM Top 10 | Red Team toolkit for AI
URL:https://github.com/DmitrL-dev/AISecurity
标签:#Red Team
更新了:Red Team
描述:AI Security Platform: Defense (217 engines) + Offense (39K+ payloads) | RLM-Toolkit: LangChain alternative with infinite context | OWASP LLM Top 10 | Red Team toolkit for AI
URL:https://github.com/DmitrL-dev/AISecurity
标签:#Red Team
GitHub监控消息提醒!!!
更新了:RCE
描述:php-in-jpg is a simple yet flexible tool that generates .jpg image files embedding PHP payloads, designed to support PHP RCE polyglot techniques.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-9932
标签:#RCE
更新了:RCE
描述:php-in-jpg is a simple yet flexible tool that generates .jpg image files embedding PHP payloads, designed to support PHP RCE polyglot techniques.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-9932
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-50498
标签:#RCE
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-50498
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2026
描述:CVE-2026-24061 - Exploit
URL:https://github.com/h3athen/CVE-2026-24061
标签:#CVE-2026
更新了:CVE-2026
描述:CVE-2026-24061 - Exploit
URL:https://github.com/h3athen/CVE-2026-24061
标签:#CVE-2026
GitHub监控消息提醒!!!
更新了:CVE-2026
描述:CVE-2026-0594 List Site Contributors Plugin Exploit
URL:https://github.com/m4sh-wacker/CVE-2026-0594-ListSiteContributors-Plugin-Exploit
标签:#CVE-2026
更新了:CVE-2026
描述:CVE-2026-0594 List Site Contributors Plugin Exploit
URL:https://github.com/m4sh-wacker/CVE-2026-0594-ListSiteContributors-Plugin-Exploit
标签:#CVE-2026
GitHub监控消息提醒!!!
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-10924
标签:#RCE
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-10924
标签:#RCE
GitHub监控消息提醒!!!
更新了:CVE-2026
描述:Exploitation of CVE-2026-24061
URL:https://github.com/SafeBreach-Labs/CVE-2026-24061
标签:#CVE-2026
更新了:CVE-2026
描述:Exploitation of CVE-2026-24061
URL:https://github.com/SafeBreach-Labs/CVE-2026-24061
标签:#CVE-2026
GitHub监控消息提醒!!!
更新了:RCE
描述:Mirage uses C++, PHP, HTML, Python, and Ansible to deploy a vulnerable IIS server capable of spawning a reverse shell and Remote Code Execution (RCE) on target machines.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-50526
标签:#RCE
更新了:RCE
描述:Mirage uses C++, PHP, HTML, Python, and Ansible to deploy a vulnerable IIS server capable of spawning a reverse shell and Remote Code Execution (RCE) on target machines.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-50526
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:🔍 Create a safe lab environment for testing CVE-2020-0610, a critical RCE vulnerability in Windows RD Gateway, with minimal disruption using DTLS techniques.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-51793
标签:#RCE
更新了:RCE
描述:🔍 Create a safe lab environment for testing CVE-2020-0610, a critical RCE vulnerability in Windows RD Gateway, with minimal disruption using DTLS techniques.
URL:https://github.com/JoshuaProvoste/0-click-RCE-Exploit-for-CVE-2024-51793
标签:#RCE
GitHub监控消息提醒!!!
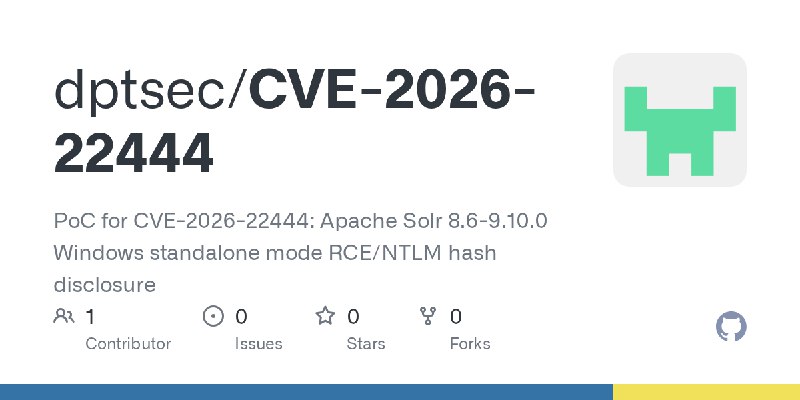
更新了:CVE-2026
描述:PoC for CVE-2026-22444: Apache Solr 8.6-9.10.0 Windows standalone mode RCE/NTLM hash disclosure
URL:https://github.com/dptsec/CVE-2026-22444
标签:#CVE-2026
更新了:CVE-2026
描述:PoC for CVE-2026-22444: Apache Solr 8.6-9.10.0 Windows standalone mode RCE/NTLM hash disclosure
URL:https://github.com/dptsec/CVE-2026-22444
标签:#CVE-2026
GitHub监控消息提醒!!!
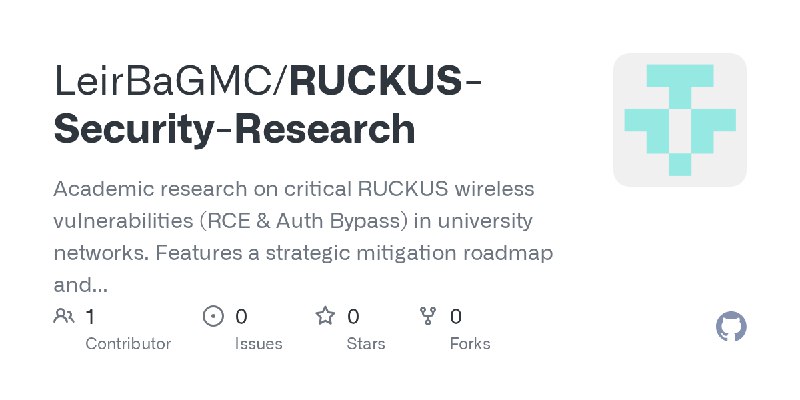
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/LeirBaGMC/RUCKUS-Security-Research
标签:#RCE
更新了:RCE
描述:Command-line post-exploitation toolkit for Microsoft SQL Server — enabling RCE, privilege escalation, persistence, and defense evasion via T-SQL.
URL:https://github.com/LeirBaGMC/RUCKUS-Security-Research
标签:#RCE
GitHub监控消息提醒!!!
更新了:RCE
描述:Repositorio para la aplicación de ingesta del RCE
URL:https://github.com/emailesc/ASIGH_IW
标签:#RCE
更新了:RCE
描述:Repositorio para la aplicación de ingesta del RCE
URL:https://github.com/emailesc/ASIGH_IW
标签:#RCE
GitHub监控消息提醒!!!
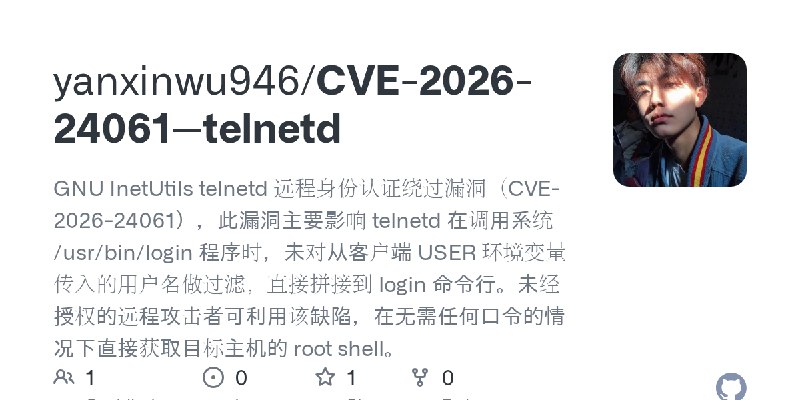
更新了:CVE-2026
描述:GNU InetUtils telnetd 远程身份认证绕过漏洞(CVE-2026-24061),此漏洞主要影响 telnetd 在调用系统 /usr/bin/login 程序时,未对从客户端 USER 环境变量传入的用户名做过滤,直接拼接到 login 命令行。未经授权的远程攻击者可利用该缺陷,在无需任何口令的情况下直接获取目标主机的 root shell。
URL:https://github.com/yanxinwu946/CVE-2026-24061--telnetd
标签:#CVE-2026
更新了:CVE-2026
描述:GNU InetUtils telnetd 远程身份认证绕过漏洞(CVE-2026-24061),此漏洞主要影响 telnetd 在调用系统 /usr/bin/login 程序时,未对从客户端 USER 环境变量传入的用户名做过滤,直接拼接到 login 命令行。未经授权的远程攻击者可利用该缺陷,在无需任何口令的情况下直接获取目标主机的 root shell。
URL:https://github.com/yanxinwu946/CVE-2026-24061--telnetd
标签:#CVE-2026
GitHub监控消息提醒!!!
更新了:RCE
描述:Command Injection / Remote Code Execution (RCE) via Insecure Deserialization in _load_ccd_pickle_cached() of chemical_components.py in AlphaFold 3 (v3.0.1) - (github.com/google-deepmind/alphafold3)
URL:https://github.com/JoshuaProvoste/Command-Injection-RCE-AlphaFold-v3.0.1
标签:#RCE
更新了:RCE
描述:Command Injection / Remote Code Execution (RCE) via Insecure Deserialization in _load_ccd_pickle_cached() of chemical_components.py in AlphaFold 3 (v3.0.1) - (github.com/google-deepmind/alphafold3)
URL:https://github.com/JoshuaProvoste/Command-Injection-RCE-AlphaFold-v3.0.1
标签:#RCE
GitHub监控消息提醒!!!
更新了:webshell
描述:🛠 Manage and deploy webshell tools for Linux using Vue 3 and Python, featuring custom traffic formats for stealthy operation.
URL:https://github.com/Richietoreck/MatouWebshell
标签:#webshell
更新了:webshell
描述:🛠 Manage and deploy webshell tools for Linux using Vue 3 and Python, featuring custom traffic formats for stealthy operation.
URL:https://github.com/Richietoreck/MatouWebshell
标签:#webshell
GitHub监控消息提醒!!!
更新了:绕过
描述:基于 Python + GitHub Actions 的博客更新监控工具,支持 Cloudflare 绕过和微信推送
URL:https://github.com/zhuyikai2002/MyPythonMoniter
标签:#绕过
更新了:绕过
描述:基于 Python + GitHub Actions 的博客更新监控工具,支持 Cloudflare 绕过和微信推送
URL:https://github.com/zhuyikai2002/MyPythonMoniter
标签:#绕过
GitHub监控消息提醒!!!
更新了:RCE
描述:Command Injection / Remote Code Execution (RCE) via Insecure Deserialization in load() of predictor.py in Vertex AI SDK v1.121.0 - (github.com/googleapis/python-aiplatform)
URL:https://github.com/JoshuaProvoste/Command-Injection-RCE-Vertex-AI-SDK-v1.121.0
标签:#RCE
更新了:RCE
描述:Command Injection / Remote Code Execution (RCE) via Insecure Deserialization in load() of predictor.py in Vertex AI SDK v1.121.0 - (github.com/googleapis/python-aiplatform)
URL:https://github.com/JoshuaProvoste/Command-Injection-RCE-Vertex-AI-SDK-v1.121.0
标签:#RCE